conduwuit
a very cool Matrix chat homeserver written in Rust
What is Matrix?
Matrix is an open, federated, and extensible network for decentralised communication. Users from any Matrix homeserver can chat with users from all other homeservers over federation. Matrix is designed to be extensible and built on top of. You can even use bridges such as Matrix Appservices to communicate with users outside of Matrix, like a community on Discord.
What is the goal?
A high-performance, efficient, low-cost, and featureful Matrix homeserver that's easy to set up and just works with minimal configuration needed.
Can I try it out?
An official conduwuit server ran by me is available at transfem.dev (element.transfem.dev / cinny.transfem.dev)
transfem.dev is a public homeserver that can be used, it is not a "test only homeserver". This means there are rules, so please read the rules: https://transfem.dev/homeserver_rules.txt
transfem.dev is also listed at servers.joinmatrix.org, which is a list of popular public Matrix homeservers, including some others that run conduwuit.
What is the current status?
conduwuit is technically a hard fork of Conduit, which is in beta. The beta status initially was inherited from Conduit, however the huge amount of codebase divergance, changes, fixes, and improvements have effectively made this beta status not entirely applicable to us anymore.
conduwuit is very stable based on our rapidly growing userbase, has lots of features that users expect, and very usable as a daily driver for small, medium, and upper-end medium sized homeservers.
A lot of critical stability and performance issues have been fixed, and a lot of necessary groundwork has finished; making this project way better than it was back in the start at ~early 2024.
Where is the differences page?
conduwuit historically had a "differences" page that listed each and every single different thing about conduwuit from Conduit, as a way to promote and advertise conduwuit by showing significant amounts of work done. While this was feasible to maintain back when the project was new in early-2024, this became impossible very quickly and has unfortunately became heavily outdated, missing tons of things, etc.
It's difficult to list out what we do differently, what are our notable features, etc when there's so many things and features and bug fixes and performance optimisations, the list goes on. We simply recommend folks to just try out conduwuit, or ask us what features you are looking for and if they're implemented in conduwuit.
How is conduwuit funded? Is conduwuit sustainable?
conduwuit has no external funding. This is made possible purely in my freetime with contributors, also in their free time, and only by user-curated donations.
conduwuit has existed since around November 2023, but only became more publicly known in March/April 2024 and we have no plans in stopping or slowing down any time soon!
Can I migrate or switch from Conduit?
conduwuit had drop-in migration/replacement support for Conduit for about 12 months before bugs somewhere along the line broke it. Maintaining this has been difficult and the majority of Conduit users have already migrated, additionally debugging Conduit is not one of our interests, and so Conduit migration no longer works. We also feel that 12 months has been plenty of time for people to seamlessly migrate.
If you are a Conduit user looking to migrate, you will have to wipe and reset your database. We may fix seamless migration support at some point, but it's not an interest from us.
Can I migrate from Synapse or Dendrite?
Currently there is no known way to seamlessly migrate all user data from the old homeserver to conduwuit. However it is perfectly acceptable to replace the old homeserver software with conduwuit using the same server name and there will not be any issues with federation.
There is an interest in developing a built-in seamless user data migration method into conduwuit, however there is no concrete ETA or timeline for this.
How can I deploy my own?
If you want to connect an appservice to conduwuit, take a look at the appservices documentation.
How can I contribute?
See the contributor's guide
Contact
#conduwuit:puppygock.gay
is the official project Matrix room. You can get support here, ask questions or
concerns, get assistance setting up conduwuit, etc.
This room should stay relevant and focused on conduwuit. An offtopic general chatter room can be found in the room topic there as well.
Please keep the issue trackers focused on actual bug reports and enhancement requests.
General support is extremely difficult to be offered over an issue tracker, and simple questions should be asked directly in an interactive platform like our Matrix room above as they can turn into a relevant discussion and/or may not be simple to answer. If you're not sure, just ask in the Matrix room.
If you have a bug or feature to request: Open an issue on GitHub
If you need to contact the primary maintainer, my contact methods are on my website: https://girlboss.ceo
Donate
conduwuit development is purely made possible by myself and contributors. I do not get paid to work on this, and I work on it in my free time. Donations are heavily appreciated! 💜🥺
- Liberapay: https://liberapay.com/girlbossceo
- GitHub Sponsors: https://github.com/sponsors/girlbossceo
- Ko-fi: https://ko-fi.com/puppygock
I do not and will not accept cryptocurrency donations, including things related.
Note that donations will NOT guarantee you or give you any kind of tangible product, feature prioritisation, etc. By donating, you are agreeing that conduwuit is NOT going to provide you any goods or services as part of your donation, and this donation is purely a generous donation. We will not provide things like paid personal/direct support, feature request priority, merchandise, etc.
Logo
Original repo and Matrix room picture was from bran (<3). Current banner image and logo is directly from this cohost post.
An SVG logo made by @nktnet1 is available here: https://github.com/girlbossceo/conduwuit/blob/main/docs/assets/
Is it conduwuit or Conduwuit?
Both, but I prefer conduwuit.
Mirrors of conduwuit
If GitHub is unavailable in your country, or has poor connectivity, conduwuit's source code is mirrored onto the following additional platforms I maintain:
- GitHub: https://github.com/girlbossceo/conduwuit
- GitLab: https://gitlab.com/conduwuit/conduwuit
- git.girlcock.ceo: https://git.girlcock.ceo/strawberry/conduwuit
- git.gay: https://git.gay/june/conduwuit
- mau.dev: https://mau.dev/june/conduwuit
- Codeberg: https://codeberg.org/arf/conduwuit
- sourcehut: https://git.sr.ht/~girlbossceo/conduwuit
Configuration
This chapter describes various ways to configure conduwuit.
Basics
conduwuit uses a config file for the majority of the settings, but also supports setting individual config options via commandline.
Please refer to the example config file for all of those settings.
The config file to use can be specified on the commandline when running
conduwuit by specifying the -c, --config flag. Alternatively, you can use
the environment variable CONDUWUIT_CONFIG to specify the config file to used.
Conduit's environment variables are supported for backwards compatibility.
Option commandline flag
conduwuit supports setting individual config options in TOML format from the
-O / --option flag. For example, you can set your server name via -O server_name=\"example.com\".
Note that the config is parsed as TOML, and shells like bash will remove quotes. So unfortunately it is required to escape quotes if the config option takes a string. This does not apply to options that take booleans or numbers:
--option allow_registration=trueworks ✅-O max_request_size=99999999works ✅-O server_name=example.comdoes not work ❌--option log=\"debug\"works ✅--option server_name='"example.com'"works ✅
Execute commandline flag
conduwuit supports running admin commands on startup using the commandline
argument --execute. The most notable use for this is to create an admin user
on first startup.
The syntax of this is a standard admin command without the prefix such as
./conduwuit --execute "users create_user june"
An example output of a success is:
INFO conduwuit_service::admin::startup: Startup command #0 completed:
Created user with user_id: @june:girlboss.ceo and password: `<redacted>`
This commandline argument can be paired with the --option flag.
Environment variables
All of the settings that are found in the config file can be specified by using
environment variables. The environment variable names should be all caps and
prefixed with CONDUWUIT_.
For example, if the setting you are changing is max_request_size, then the
environment variable to set is CONDUWUIT_MAX_REQUEST_SIZE.
To modify config options not in the [global] context such as
[global.well_known], use the __ suffix split: CONDUWUIT_WELL_KNOWN__SERVER
Conduit's environment variables are supported for backwards compatibility (e.g.
CONDUIT_SERVER_NAME).
Example configuration
Example configuration
### conduwuit Configuration
###
### THIS FILE IS GENERATED. CHANGES/CONTRIBUTIONS IN THE REPO WILL BE
### OVERWRITTEN!
###
### You should rename this file before configuring your server. Changes to
### documentation and defaults can be contributed in source code at
### src/core/config/mod.rs. This file is generated when building.
###
### Any values pre-populated are the default values for said config option.
###
### At the minimum, you MUST edit all the config options to your environment
### that say "YOU NEED TO EDIT THIS".
###
### For more information, see:
### https://conduwuit.puppyirl.gay/configuration.html
[global]
# The server_name is the pretty name of this server. It is used as a
# suffix for user and room IDs/aliases.
#
# See the docs for reverse proxying and delegation:
# https://conduwuit.puppyirl.gay/deploying/generic.html#setting-up-the-reverse-proxy
#
# Also see the `[global.well_known]` config section at the very bottom.
#
# Examples of delegation:
# - https://puppygock.gay/.well-known/matrix/server
# - https://puppygock.gay/.well-known/matrix/client
#
# YOU NEED TO EDIT THIS. THIS CANNOT BE CHANGED AFTER WITHOUT A DATABASE
# WIPE.
#
# example: "conduwuit.woof"
#
#server_name =
# The default address (IPv4 or IPv6) conduwuit will listen on.
#
# If you are using Docker or a container NAT networking setup, this must
# be "0.0.0.0".
#
# To listen on multiple addresses, specify a vector e.g. ["127.0.0.1",
# "::1"]
#
#address = ["127.0.0.1", "::1"]
# The port(s) conduwuit will listen on.
#
# For reverse proxying, see:
# https://conduwuit.puppyirl.gay/deploying/generic.html#setting-up-the-reverse-proxy
#
# If you are using Docker, don't change this, you'll need to map an
# external port to this.
#
# To listen on multiple ports, specify a vector e.g. [8080, 8448]
#
#port = 8008
# The UNIX socket conduwuit will listen on.
#
# conduwuit cannot listen on both an IP address and a UNIX socket. If
# listening on a UNIX socket, you MUST remove/comment the `address` key.
#
# Remember to make sure that your reverse proxy has access to this socket
# file, either by adding your reverse proxy to the 'conduwuit' group or
# granting world R/W permissions with `unix_socket_perms` (666 minimum).
#
# example: "/run/conduwuit/conduwuit.sock"
#
#unix_socket_path =
# The default permissions (in octal) to create the UNIX socket with.
#
#unix_socket_perms = 660
# This is the only directory where conduwuit will save its data, including
# media. Note: this was previously "/var/lib/matrix-conduit".
#
# YOU NEED TO EDIT THIS.
#
# example: "/var/lib/conduwuit"
#
#database_path =
# conduwuit supports online database backups using RocksDB's Backup engine
# API. To use this, set a database backup path that conduwuit can write
# to.
#
# For more information, see:
# https://conduwuit.puppyirl.gay/maintenance.html#backups
#
# example: "/opt/conduwuit-db-backups"
#
#database_backup_path =
# The amount of online RocksDB database backups to keep/retain, if using
# "database_backup_path", before deleting the oldest one.
#
#database_backups_to_keep = 1
# Text which will be added to the end of the user's displayname upon
# registration with a space before the text. In Conduit, this was the
# lightning bolt emoji.
#
# To disable, set this to "" (an empty string).
#
# The default is the trans pride flag.
#
# example: "🏳️⚧️"
#
#new_user_displayname_suffix = "🏳️⚧️"
# If enabled, conduwuit will send a simple GET request periodically to
# `https://pupbrain.dev/check-for-updates/stable` for any new
# announcements made. Despite the name, this is not an update check
# endpoint, it is simply an announcement check endpoint.
#
# This is disabled by default as this is rarely used except for security
# updates or major updates.
#
#allow_check_for_updates = false
# Set this to any float value to multiply conduwuit's in-memory LRU caches
# with such as "auth_chain_cache_capacity".
#
# May be useful if you have significant memory to spare to increase
# performance.
#
# If you have low memory, reducing this may be viable.
#
# By default, the individual caches such as "auth_chain_cache_capacity"
# are scaled by your CPU core count.
#
#cache_capacity_modifier = 1.0
# Set this to any float value in megabytes for conduwuit to tell the
# database engine that this much memory is available for database read
# caches.
#
# May be useful if you have significant memory to spare to increase
# performance.
#
# Similar to the individual LRU caches, this is scaled up with your CPU
# core count.
#
# This defaults to 128.0 + (64.0 * CPU core count).
#
#db_cache_capacity_mb = varies by system
# Set this to any float value in megabytes for conduwuit to tell the
# database engine that this much memory is available for database write
# caches.
#
# May be useful if you have significant memory to spare to increase
# performance.
#
# Similar to the individual LRU caches, this is scaled up with your CPU
# core count.
#
# This defaults to 48.0 + (4.0 * CPU core count).
#
#db_write_buffer_capacity_mb = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#pdu_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#auth_chain_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#shorteventid_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#eventidshort_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#eventid_pdu_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#shortstatekey_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#statekeyshort_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#servernameevent_data_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#server_visibility_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#user_visibility_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#stateinfo_cache_capacity = varies by system
# This item is undocumented. Please contribute documentation for it.
#
#roomid_spacehierarchy_cache_capacity = varies by system
# Maximum entries stored in DNS memory-cache. The size of an entry may
# vary so please take care if raising this value excessively. Only
# decrease this when using an external DNS cache. Please note that
# systemd-resolved does *not* count as an external cache, even when
# configured to do so.
#
#dns_cache_entries = 32768
# Minimum time-to-live in seconds for entries in the DNS cache. The
# default may appear high to most administrators; this is by design as the
# majority of NXDOMAINs are correct for a long time (e.g. the server is no
# longer running Matrix). Only decrease this if you are using an external
# DNS cache.
#
#dns_min_ttl = 10800
# Minimum time-to-live in seconds for NXDOMAIN entries in the DNS cache.
# This value is critical for the server to federate efficiently.
# NXDOMAIN's are assumed to not be returning to the federation and
# aggressively cached rather than constantly rechecked.
#
# Defaults to 3 days as these are *very rarely* false negatives.
#
#dns_min_ttl_nxdomain = 259200
# Number of DNS nameserver retries after a timeout or error.
#
#dns_attempts = 10
# The number of seconds to wait for a reply to a DNS query. Please note
# that recursive queries can take up to several seconds for some domains,
# so this value should not be too low, especially on slower hardware or
# resolvers.
#
#dns_timeout = 10
# Fallback to TCP on DNS errors. Set this to false if unsupported by
# nameserver.
#
#dns_tcp_fallback = true
# Enable to query all nameservers until the domain is found. Referred to
# as "trust_negative_responses" in hickory_resolver. This can avoid
# useless DNS queries if the first nameserver responds with NXDOMAIN or
# an empty NOERROR response.
#
#query_all_nameservers = true
# Enable using *only* TCP for querying your specified nameservers instead
# of UDP.
#
# If you are running conduwuit in a container environment, this config
# option may need to be enabled. For more details, see:
# https://conduwuit.puppyirl.gay/troubleshooting.html#potential-dns-issues-when-using-docker
#
#query_over_tcp_only = false
# DNS A/AAAA record lookup strategy
#
# Takes a number of one of the following options:
# 1 - Ipv4Only (Only query for A records, no AAAA/IPv6)
#
# 2 - Ipv6Only (Only query for AAAA records, no A/IPv4)
#
# 3 - Ipv4AndIpv6 (Query for A and AAAA records in parallel, uses whatever
# returns a successful response first)
#
# 4 - Ipv6thenIpv4 (Query for AAAA record, if that fails then query the A
# record)
#
# 5 - Ipv4thenIpv6 (Query for A record, if that fails then query the AAAA
# record)
#
# If you don't have IPv6 networking, then for better DNS performance it
# may be suitable to set this to Ipv4Only (1) as you will never ever use
# the AAAA record contents even if the AAAA record is successful instead
# of the A record.
#
#ip_lookup_strategy = 5
# Max request size for file uploads in bytes. Defaults to 20MB.
#
#max_request_size = 20971520
# This item is undocumented. Please contribute documentation for it.
#
#max_fetch_prev_events = 192
# Default/base connection timeout (seconds). This is used only by URL
# previews and update/news endpoint checks.
#
#request_conn_timeout = 10
# Default/base request timeout (seconds). The time waiting to receive more
# data from another server. This is used only by URL previews,
# update/news, and misc endpoint checks.
#
#request_timeout = 35
# Default/base request total timeout (seconds). The time limit for a whole
# request. This is set very high to not cancel healthy requests while
# serving as a backstop. This is used only by URL previews and update/news
# endpoint checks.
#
#request_total_timeout = 320
# Default/base idle connection pool timeout (seconds). This is used only
# by URL previews and update/news endpoint checks.
#
#request_idle_timeout = 5
# Default/base max idle connections per host. This is used only by URL
# previews and update/news endpoint checks. Defaults to 1 as generally the
# same open connection can be re-used.
#
#request_idle_per_host = 1
# Federation well-known resolution connection timeout (seconds).
#
#well_known_conn_timeout = 6
# Federation HTTP well-known resolution request timeout (seconds).
#
#well_known_timeout = 10
# Federation client request timeout (seconds). You most definitely want
# this to be high to account for extremely large room joins, slow
# homeservers, your own resources etc.
#
#federation_timeout = 300
# Federation client idle connection pool timeout (seconds).
#
#federation_idle_timeout = 25
# Federation client max idle connections per host. Defaults to 1 as
# generally the same open connection can be re-used.
#
#federation_idle_per_host = 1
# Federation sender request timeout (seconds). The time it takes for the
# remote server to process sent transactions can take a while.
#
#sender_timeout = 180
# Federation sender idle connection pool timeout (seconds).
#
#sender_idle_timeout = 180
# Federation sender transaction retry backoff limit (seconds).
#
#sender_retry_backoff_limit = 86400
# Appservice URL request connection timeout. Defaults to 35 seconds as
# generally appservices are hosted within the same network.
#
#appservice_timeout = 35
# Appservice URL idle connection pool timeout (seconds).
#
#appservice_idle_timeout = 300
# Notification gateway pusher idle connection pool timeout.
#
#pusher_idle_timeout = 15
# Maximum time to receive a request from a client (seconds).
#
#client_receive_timeout = 75
# Maximum time to process a request received from a client (seconds).
#
#client_request_timeout = 180
# Maximum time to transmit a response to a client (seconds)
#
#client_response_timeout = 120
# Grace period for clean shutdown of client requests (seconds).
#
#client_shutdown_timeout = 10
# Grace period for clean shutdown of federation requests (seconds).
#
#sender_shutdown_timeout = 5
# Enables registration. If set to false, no users can register on this
# server.
#
# If set to true without a token configured, users can register with no
# form of 2nd-step only if you set the following option to true:
# `yes_i_am_very_very_sure_i_want_an_open_registration_server_prone_to_abuse`
#
# If you would like registration only via token reg, please configure
# `registration_token` or `registration_token_file`.
#
#allow_registration = false
# Enabling this setting opens registration to anyone without restrictions.
# This makes your server vulnerable to abuse
#
#yes_i_am_very_very_sure_i_want_an_open_registration_server_prone_to_abuse = false
# A static registration token that new users will have to provide when
# creating an account. If unset and `allow_registration` is true,
# you must set
# `yes_i_am_very_very_sure_i_want_an_open_registration_server_prone_to_abuse`
# to true to allow open registration without any conditions.
#
# YOU NEED TO EDIT THIS OR USE registration_token_file.
#
# example: "o&^uCtes4HPf0Vu@F20jQeeWE7"
#
#registration_token =
# Path to a file on the system that gets read for additional registration
# tokens. Multiple tokens can be added if you separate them with
# whitespace
#
# conduwuit must be able to access the file, and it must not be empty
#
# example: "/etc/conduwuit/.reg_token"
#
#registration_token_file =
# Controls whether encrypted rooms and events are allowed.
#
#allow_encryption = true
# Controls whether federation is allowed or not. It is not recommended to
# disable this after the fact due to potential federation breakage.
#
#allow_federation = true
# Allows federation requests to be made to itself
#
# This isn't intended and is very likely a bug if federation requests are
# being sent to yourself. This currently mainly exists for development
# purposes.
#
#federation_loopback = false
# Always calls /forget on behalf of the user if leaving a room. This is a
# part of MSC4267 "Automatically forgetting rooms on leave"
#
#forget_forced_upon_leave = false
# Set this to true to require authentication on the normally
# unauthenticated profile retrieval endpoints (GET)
# "/_matrix/client/v3/profile/{userId}".
#
# This can prevent profile scraping.
#
#require_auth_for_profile_requests = false
# Set this to true to allow your server's public room directory to be
# federated. Set this to false to protect against /publicRooms spiders,
# but will forbid external users from viewing your server's public room
# directory. If federation is disabled entirely (`allow_federation`), this
# is inherently false.
#
#allow_public_room_directory_over_federation = false
# Set this to true to allow your server's public room directory to be
# queried without client authentication (access token) through the Client
# APIs. Set this to false to protect against /publicRooms spiders.
#
#allow_public_room_directory_without_auth = false
# Allow guests/unauthenticated users to access TURN credentials.
#
# This is the equivalent of Synapse's `turn_allow_guests` config option.
# This allows any unauthenticated user to call the endpoint
# `/_matrix/client/v3/voip/turnServer`.
#
# It is unlikely you need to enable this as all major clients support
# authentication for this endpoint and prevents misuse of your TURN server
# from potential bots.
#
#turn_allow_guests = false
# Set this to true to lock down your server's public room directory and
# only allow admins to publish rooms to the room directory. Unpublishing
# is still allowed by all users with this enabled.
#
#lockdown_public_room_directory = false
# Set this to true to allow federating device display names / allow
# external users to see your device display name. If federation is
# disabled entirely (`allow_federation`), this is inherently false. For
# privacy reasons, this is best left disabled.
#
#allow_device_name_federation = false
# Config option to allow or disallow incoming federation requests that
# obtain the profiles of our local users from
# `/_matrix/federation/v1/query/profile`
#
# Increases privacy of your local user's such as display names, but some
# remote users may get a false "this user does not exist" error when they
# try to invite you to a DM or room. Also can protect against profile
# spiders.
#
# This is inherently false if `allow_federation` is disabled
#
#allow_inbound_profile_lookup_federation_requests = true
# Allow standard users to create rooms. Appservices and admins are always
# allowed to create rooms
#
#allow_room_creation = true
# Set to false to disable users from joining or creating room versions
# that aren't officially supported by conduwuit.
#
# conduwuit officially supports room versions 6 - 11.
#
# conduwuit has slightly experimental (though works fine in practice)
# support for versions 3 - 5.
#
#allow_unstable_room_versions = true
# Default room version conduwuit will create rooms with.
#
# Per spec, room version 10 is the default.
#
#default_room_version = 10
# This item is undocumented. Please contribute documentation for it.
#
#allow_jaeger = false
# This item is undocumented. Please contribute documentation for it.
#
#jaeger_filter = "info"
# If the 'perf_measurements' compile-time feature is enabled, enables
# collecting folded stack trace profile of tracing spans using
# tracing_flame. The resulting profile can be visualized with inferno[1],
# speedscope[2], or a number of other tools.
#
# [1]: https://github.com/jonhoo/inferno
# [2]: www.speedscope.app
#
#tracing_flame = false
# This item is undocumented. Please contribute documentation for it.
#
#tracing_flame_filter = "info"
# This item is undocumented. Please contribute documentation for it.
#
#tracing_flame_output_path = "./tracing.folded"
# Examples:
#
# - No proxy (default):
#
# proxy = "none"
#
# - For global proxy, create the section at the bottom of this file:
#
# [global.proxy]
# global = { url = "socks5h://localhost:9050" }
#
# - To proxy some domains:
#
# [global.proxy]
# [[global.proxy.by_domain]]
# url = "socks5h://localhost:9050"
# include = ["*.onion", "matrix.myspecial.onion"]
# exclude = ["*.myspecial.onion"]
#
# Include vs. Exclude:
#
# - If include is an empty list, it is assumed to be `["*"]`.
#
# - If a domain matches both the exclude and include list, the proxy will
# only be used if it was included because of a more specific rule than
# it was excluded. In the above example, the proxy would be used for
# `ordinary.onion`, `matrix.myspecial.onion`, but not
# `hello.myspecial.onion`.
#
#proxy = "none"
# Servers listed here will be used to gather public keys of other servers
# (notary trusted key servers).
#
# Currently, conduwuit doesn't support inbound batched key requests, so
# this list should only contain other Synapse servers.
#
# example: ["matrix.org", "envs.net", "tchncs.de"]
#
#trusted_servers = ["matrix.org"]
# Whether to query the servers listed in trusted_servers first or query
# the origin server first. For best security, querying the origin server
# first is advised to minimize the exposure to a compromised trusted
# server. For maximum federation/join performance this can be set to true,
# however other options exist to query trusted servers first under
# specific high-load circumstances and should be evaluated before setting
# this to true.
#
#query_trusted_key_servers_first = false
# Whether to query the servers listed in trusted_servers first
# specifically on room joins. This option limits the exposure to a
# compromised trusted server to room joins only. The join operation
# requires gathering keys from many origin servers which can cause
# significant delays. Therefor this defaults to true to mitigate
# unexpected delays out-of-the-box. The security-paranoid or those willing
# to tolerate delays are advised to set this to false. Note that setting
# query_trusted_key_servers_first to true causes this option to be
# ignored.
#
#query_trusted_key_servers_first_on_join = true
# Only query trusted servers for keys and never the origin server. This is
# intended for clusters or custom deployments using their trusted_servers
# as forwarding-agents to cache and deduplicate requests. Notary servers
# do not act as forwarding-agents by default, therefor do not enable this
# unless you know exactly what you are doing.
#
#only_query_trusted_key_servers = false
# Maximum number of keys to request in each trusted server batch query.
#
#trusted_server_batch_size = 1024
# Max log level for conduwuit. Allows debug, info, warn, or error.
#
# See also:
# https://docs.rs/tracing-subscriber/latest/tracing_subscriber/filter/struct.EnvFilter.html#directives
#
# **Caveat**:
# For release builds, the tracing crate is configured to only implement
# levels higher than error to avoid unnecessary overhead in the compiled
# binary from trace macros. For debug builds, this restriction is not
# applied.
#
#log = "info"
# Output logs with ANSI colours.
#
#log_colors = true
# Configures the span events which will be outputted with the log.
#
#log_span_events = "none"
# Configures whether CONDUWUIT_LOG EnvFilter matches values using regular
# expressions. See the tracing_subscriber documentation on Directives.
#
#log_filter_regex = true
# Toggles the display of ThreadId in tracing log output.
#
#log_thread_ids = false
# OpenID token expiration/TTL in seconds.
#
# These are the OpenID tokens that are primarily used for Matrix account
# integrations (e.g. Vector Integrations in Element), *not* OIDC/OpenID
# Connect/etc.
#
#openid_token_ttl = 3600
# Allow an existing session to mint a login token for another client.
# This requires interactive authentication, but has security ramifications
# as a malicious client could use the mechanism to spawn more than one
# session.
# Enabled by default.
#
#login_via_existing_session = true
# Login token expiration/TTL in milliseconds.
#
# These are short-lived tokens for the m.login.token endpoint.
# This is used to allow existing sessions to create new sessions.
# see login_via_existing_session.
#
#login_token_ttl = 120000
# Static TURN username to provide the client if not using a shared secret
# ("turn_secret"), It is recommended to use a shared secret over static
# credentials.
#
#turn_username = false
# Static TURN password to provide the client if not using a shared secret
# ("turn_secret"). It is recommended to use a shared secret over static
# credentials.
#
#turn_password = false
# Vector list of TURN URIs/servers to use.
#
# Replace "example.turn.uri" with your TURN domain, such as the coturn
# "realm" config option. If using TURN over TLS, replace the URI prefix
# "turn:" with "turns:".
#
# example: ["turn:example.turn.uri?transport=udp",
# "turn:example.turn.uri?transport=tcp"]
#
#turn_uris = []
# TURN secret to use for generating the HMAC-SHA1 hash apart of username
# and password generation.
#
# This is more secure, but if needed you can use traditional static
# username/password credentials.
#
#turn_secret = false
# TURN secret to use that's read from the file path specified.
#
# This takes priority over "turn_secret" first, and falls back to
# "turn_secret" if invalid or failed to open.
#
# example: "/etc/conduwuit/.turn_secret"
#
#turn_secret_file =
# TURN TTL, in seconds.
#
#turn_ttl = 86400
# List/vector of room IDs or room aliases that conduwuit will make newly
# registered users join. The rooms specified must be rooms that you have
# joined at least once on the server, and must be public.
#
# example: ["#conduwuit:puppygock.gay",
# "!eoIzvAvVwY23LPDay8:puppygock.gay"]
#
#auto_join_rooms = []
# Config option to automatically deactivate the account of any user who
# attempts to join a:
# - banned room
# - forbidden room alias
# - room alias or ID with a forbidden server name
#
# This may be useful if all your banned lists consist of toxic rooms or
# servers that no good faith user would ever attempt to join, and
# to automatically remediate the problem without any admin user
# intervention.
#
# This will also make the user leave all rooms. Federation (e.g. remote
# room invites) are ignored here.
#
# Defaults to false as rooms can be banned for non-moderation-related
# reasons and this performs a full user deactivation.
#
#auto_deactivate_banned_room_attempts = false
# RocksDB log level. This is not the same as conduwuit's log level. This
# is the log level for the RocksDB engine/library which show up in your
# database folder/path as `LOG` files. conduwuit will log RocksDB errors
# as normal through tracing or panics if severe for safety.
#
#rocksdb_log_level = "error"
# This item is undocumented. Please contribute documentation for it.
#
#rocksdb_log_stderr = false
# Max RocksDB `LOG` file size before rotating in bytes. Defaults to 4MB in
# bytes.
#
#rocksdb_max_log_file_size = 4194304
# Time in seconds before RocksDB will forcibly rotate logs.
#
#rocksdb_log_time_to_roll = 0
# Set this to true to use RocksDB config options that are tailored to HDDs
# (slower device storage).
#
# It is worth noting that by default, conduwuit will use RocksDB with
# Direct IO enabled. *Generally* speaking this improves performance as it
# bypasses buffered I/O (system page cache). However there is a potential
# chance that Direct IO may cause issues with database operations if your
# setup is uncommon. This has been observed with FUSE filesystems, and
# possibly ZFS filesystem. RocksDB generally deals/corrects these issues
# but it cannot account for all setups. If you experience any weird
# RocksDB issues, try enabling this option as it turns off Direct IO and
# feel free to report in the conduwuit Matrix room if this option fixes
# your DB issues.
#
# For more information, see:
# https://github.com/facebook/rocksdb/wiki/Direct-IO
#
#rocksdb_optimize_for_spinning_disks = false
# Enables direct-io to increase database performance via unbuffered I/O.
#
# For more details about direct I/O and RockDB, see:
# https://github.com/facebook/rocksdb/wiki/Direct-IO
#
# Set this option to false if the database resides on a filesystem which
# does not support direct-io like FUSE, or any form of complex filesystem
# setup such as possibly ZFS.
#
#rocksdb_direct_io = true
# Amount of threads that RocksDB will use for parallelism on database
# operations such as cleanup, sync, flush, compaction, etc. Set to 0 to
# use all your logical threads. Defaults to your CPU logical thread count.
#
#rocksdb_parallelism_threads = varies by system
# Maximum number of LOG files RocksDB will keep. This must *not* be set to
# 0. It must be at least 1. Defaults to 3 as these are not very useful
# unless troubleshooting/debugging a RocksDB bug.
#
#rocksdb_max_log_files = 3
# Type of RocksDB database compression to use.
#
# Available options are "zstd", "bz2", "lz4", or "none".
#
# It is best to use ZSTD as an overall good balance between
# speed/performance, storage, IO amplification, and CPU usage. For more
# performance but less compression (more storage used) and less CPU usage,
# use LZ4.
#
# For more details, see:
# https://github.com/facebook/rocksdb/wiki/Compression
#
# "none" will disable compression.
#
#rocksdb_compression_algo = "zstd"
# Level of compression the specified compression algorithm for RocksDB to
# use.
#
# Default is 32767, which is internally read by RocksDB as the default
# magic number and translated to the library's default compression level
# as they all differ. See their `kDefaultCompressionLevel`.
#
# Note when using the default value we may override it with a setting
# tailored specifically conduwuit.
#
#rocksdb_compression_level = 32767
# Level of compression the specified compression algorithm for the
# bottommost level/data for RocksDB to use. Default is 32767, which is
# internally read by RocksDB as the default magic number and translated to
# the library's default compression level as they all differ. See their
# `kDefaultCompressionLevel`.
#
# Since this is the bottommost level (generally old and least used data),
# it may be desirable to have a very high compression level here as it's
# less likely for this data to be used. Research your chosen compression
# algorithm.
#
# Note when using the default value we may override it with a setting
# tailored specifically conduwuit.
#
#rocksdb_bottommost_compression_level = 32767
# Whether to enable RocksDB's "bottommost_compression".
#
# At the expense of more CPU usage, this will further compress the
# database to reduce more storage. It is recommended to use ZSTD
# compression with this for best compression results. This may be useful
# if you're trying to reduce storage usage from the database.
#
# See https://github.com/facebook/rocksdb/wiki/Compression for more details.
#
#rocksdb_bottommost_compression = true
# Database recovery mode (for RocksDB WAL corruption).
#
# Use this option when the server reports corruption and refuses to start.
# Set mode 2 (PointInTime) to cleanly recover from this corruption. The
# server will continue from the last good state, several seconds or
# minutes prior to the crash. Clients may have to run "clear-cache &
# reload" to account for the rollback. Upon success, you may reset the
# mode back to default and restart again. Please note in some cases the
# corruption error may not be cleared for at least 30 minutes of operation
# in PointInTime mode.
#
# As a very last ditch effort, if PointInTime does not fix or resolve
# anything, you can try mode 3 (SkipAnyCorruptedRecord) but this will
# leave the server in a potentially inconsistent state.
#
# The default mode 1 (TolerateCorruptedTailRecords) will automatically
# drop the last entry in the database if corrupted during shutdown, but
# nothing more. It is extraordinarily unlikely this will desynchronize
# clients. To disable any form of silent rollback set mode 0
# (AbsoluteConsistency).
#
# The options are:
# 0 = AbsoluteConsistency
# 1 = TolerateCorruptedTailRecords (default)
# 2 = PointInTime (use me if trying to recover)
# 3 = SkipAnyCorruptedRecord (you now voided your Conduwuit warranty)
#
# For more information on these modes, see:
# https://github.com/facebook/rocksdb/wiki/WAL-Recovery-Modes
#
# For more details on recovering a corrupt database, see:
# https://conduwuit.puppyirl.gay/troubleshooting.html#database-corruption
#
#rocksdb_recovery_mode = 1
# Enables or disables paranoid SST file checks. This can improve RocksDB
# database consistency at a potential performance impact due to further
# safety checks ran.
#
# For more information, see:
# https://github.com/facebook/rocksdb/wiki/Online-Verification#columnfamilyoptionsparanoid_file_checks
#
#rocksdb_paranoid_file_checks = false
# Enables or disables checksum verification in rocksdb at runtime.
# Checksums are usually hardware accelerated with low overhead; they are
# enabled in rocksdb by default. Older or slower platforms may see gains
# from disabling.
#
#rocksdb_checksums = true
# Enables the "atomic flush" mode in rocksdb. This option is not intended
# for users. It may be removed or ignored in future versions. Atomic flush
# may be enabled by the paranoid to possibly improve database integrity at
# the cost of performance.
#
#rocksdb_atomic_flush = false
# Database repair mode (for RocksDB SST corruption).
#
# Use this option when the server reports corruption while running or
# panics. If the server refuses to start use the recovery mode options
# first. Corruption errors containing the acronym 'SST' which occur after
# startup will likely require this option.
#
# - Backing up your database directory is recommended prior to running the
# repair.
#
# - Disabling repair mode and restarting the server is recommended after
# running the repair.
#
# See https://conduwuit.puppyirl.gay/troubleshooting.html#database-corruption for more details on recovering a corrupt database.
#
#rocksdb_repair = false
# This item is undocumented. Please contribute documentation for it.
#
#rocksdb_read_only = false
# This item is undocumented. Please contribute documentation for it.
#
#rocksdb_secondary = false
# Enables idle CPU priority for compaction thread. This is not enabled by
# default to prevent compaction from falling too far behind on busy
# systems.
#
#rocksdb_compaction_prio_idle = false
# Enables idle IO priority for compaction thread. This prevents any
# unexpected lag in the server's operation and is usually a good idea.
# Enabled by default.
#
#rocksdb_compaction_ioprio_idle = true
# Disables RocksDB compaction. You should never ever have to set this
# option to true. If you for some reason find yourself needing to use this
# option as part of troubleshooting or a bug, please reach out to us in
# the conduwuit Matrix room with information and details.
#
# Disabling compaction will lead to a significantly bloated and
# explosively large database, gradually poor performance, unnecessarily
# excessive disk read/writes, and slower shutdowns and startups.
#
#rocksdb_compaction = true
# Level of statistics collection. Some admin commands to display database
# statistics may require this option to be set. Database performance may
# be impacted by higher settings.
#
# Option is a number ranging from 0 to 6:
# 0 = No statistics.
# 1 = No statistics in release mode (default).
# 2 to 3 = Statistics with no performance impact.
# 3 to 5 = Statistics with possible performance impact.
# 6 = All statistics.
#
#rocksdb_stats_level = 1
# This is a password that can be configured that will let you login to the
# server bot account (currently `@conduit`) for emergency troubleshooting
# purposes such as recovering/recreating your admin room, or inviting
# yourself back.
#
# See https://conduwuit.puppyirl.gay/troubleshooting.html#lost-access-to-admin-room for other ways to get back into your admin room.
#
# Once this password is unset, all sessions will be logged out for
# security purposes.
#
# example: "F670$2CP@Hw8mG7RY1$%!#Ic7YA"
#
#emergency_password =
# This item is undocumented. Please contribute documentation for it.
#
#notification_push_path = "/_matrix/push/v1/notify"
# Allow local (your server only) presence updates/requests.
#
# Note that presence on conduwuit is very fast unlike Synapse's. If using
# outgoing presence, this MUST be enabled.
#
#allow_local_presence = true
# Allow incoming federated presence updates/requests.
#
# This option receives presence updates from other servers, but does not
# send any unless `allow_outgoing_presence` is true. Note that presence on
# conduwuit is very fast unlike Synapse's.
#
#allow_incoming_presence = true
# Allow outgoing presence updates/requests.
#
# This option sends presence updates to other servers, but does not
# receive any unless `allow_incoming_presence` is true. Note that presence
# on conduwuit is very fast unlike Synapse's. If using outgoing presence,
# you MUST enable `allow_local_presence` as well.
#
#allow_outgoing_presence = true
# How many seconds without presence updates before you become idle.
# Defaults to 5 minutes.
#
#presence_idle_timeout_s = 300
# How many seconds without presence updates before you become offline.
# Defaults to 30 minutes.
#
#presence_offline_timeout_s = 1800
# Enable the presence idle timer for remote users.
#
# Disabling is offered as an optimization for servers participating in
# many large rooms or when resources are limited. Disabling it may cause
# incorrect presence states (i.e. stuck online) to be seen for some remote
# users.
#
#presence_timeout_remote_users = true
# Allow receiving incoming read receipts from remote servers.
#
#allow_incoming_read_receipts = true
# Allow sending read receipts to remote servers.
#
#allow_outgoing_read_receipts = true
# Allow outgoing typing updates to federation.
#
#allow_outgoing_typing = true
# Allow incoming typing updates from federation.
#
#allow_incoming_typing = true
# Maximum time federation user can indicate typing.
#
#typing_federation_timeout_s = 30
# Minimum time local client can indicate typing. This does not override a
# client's request to stop typing. It only enforces a minimum value in
# case of no stop request.
#
#typing_client_timeout_min_s = 15
# Maximum time local client can indicate typing.
#
#typing_client_timeout_max_s = 45
# Set this to true for conduwuit to compress HTTP response bodies using
# zstd. This option does nothing if conduwuit was not built with
# `zstd_compression` feature. Please be aware that enabling HTTP
# compression may weaken TLS. Most users should not need to enable this.
# See https://breachattack.com/ and https://wikipedia.org/wiki/BREACH
# before deciding to enable this.
#
#zstd_compression = false
# Set this to true for conduwuit to compress HTTP response bodies using
# gzip. This option does nothing if conduwuit was not built with
# `gzip_compression` feature. Please be aware that enabling HTTP
# compression may weaken TLS. Most users should not need to enable this.
# See https://breachattack.com/ and https://wikipedia.org/wiki/BREACH before
# deciding to enable this.
#
# If you are in a large amount of rooms, you may find that enabling this
# is necessary to reduce the significantly large response bodies.
#
#gzip_compression = false
# Set this to true for conduwuit to compress HTTP response bodies using
# brotli. This option does nothing if conduwuit was not built with
# `brotli_compression` feature. Please be aware that enabling HTTP
# compression may weaken TLS. Most users should not need to enable this.
# See https://breachattack.com/ and https://wikipedia.org/wiki/BREACH
# before deciding to enable this.
#
#brotli_compression = false
# Set to true to allow user type "guest" registrations. Some clients like
# Element attempt to register guest users automatically.
#
#allow_guest_registration = false
# Set to true to log guest registrations in the admin room. Note that
# these may be noisy or unnecessary if you're a public homeserver.
#
#log_guest_registrations = false
# Set to true to allow guest registrations/users to auto join any rooms
# specified in `auto_join_rooms`.
#
#allow_guests_auto_join_rooms = false
# Enable the legacy unauthenticated Matrix media repository endpoints.
# These endpoints consist of:
# - /_matrix/media/*/config
# - /_matrix/media/*/upload
# - /_matrix/media/*/preview_url
# - /_matrix/media/*/download/*
# - /_matrix/media/*/thumbnail/*
#
# The authenticated equivalent endpoints are always enabled.
#
# Defaults to true for now, but this is highly subject to change, likely
# in the next release.
#
#allow_legacy_media = true
# This item is undocumented. Please contribute documentation for it.
#
#freeze_legacy_media = true
# Check consistency of the media directory at startup:
# 1. When `media_compat_file_link` is enabled, this check will upgrade
# media when switching back and forth between Conduit and conduwuit.
# Both options must be enabled to handle this.
# 2. When media is deleted from the directory, this check will also delete
# its database entry.
#
# If none of these checks apply to your use cases, and your media
# directory is significantly large setting this to false may reduce
# startup time.
#
#media_startup_check = true
# Enable backward-compatibility with Conduit's media directory by creating
# symlinks of media.
#
# This option is only necessary if you plan on using Conduit again.
# Otherwise setting this to false reduces filesystem clutter and overhead
# for managing these symlinks in the directory. This is now disabled by
# default. You may still return to upstream Conduit but you have to run
# conduwuit at least once with this set to true and allow the
# media_startup_check to take place before shutting down to return to
# Conduit.
#
#media_compat_file_link = false
# Prune missing media from the database as part of the media startup
# checks.
#
# This means if you delete files from the media directory the
# corresponding entries will be removed from the database. This is
# disabled by default because if the media directory is accidentally moved
# or inaccessible, the metadata entries in the database will be lost with
# sadness.
#
#prune_missing_media = false
# Vector list of servers that conduwuit will refuse to download remote
# media from.
#
#prevent_media_downloads_from = []
# List of forbidden server names that we will block incoming AND outgoing
# federation with, and block client room joins / remote user invites.
#
# This check is applied on the room ID, room alias, sender server name,
# sender user's server name, inbound federation X-Matrix origin, and
# outbound federation handler.
#
# Basically "global" ACLs.
#
#forbidden_remote_server_names = []
# List of forbidden server names that we will block all outgoing federated
# room directory requests for. Useful for preventing our users from
# wandering into bad servers or spaces.
#
#forbidden_remote_room_directory_server_names = []
# Vector list of IPv4 and IPv6 CIDR ranges / subnets *in quotes* that you
# do not want conduwuit to send outbound requests to. Defaults to
# RFC1918, unroutable, loopback, multicast, and testnet addresses for
# security.
#
# Please be aware that this is *not* a guarantee. You should be using a
# firewall with zones as doing this on the application layer may have
# bypasses.
#
# Currently this does not account for proxies in use like Synapse does.
#
# To disable, set this to be an empty vector (`[]`).
#
# Defaults to:
# ["127.0.0.0/8", "10.0.0.0/8", "172.16.0.0/12",
# "192.168.0.0/16", "100.64.0.0/10", "192.0.0.0/24", "169.254.0.0/16",
# "192.88.99.0/24", "198.18.0.0/15", "192.0.2.0/24", "198.51.100.0/24",
# "203.0.113.0/24", "224.0.0.0/4", "::1/128", "fe80::/10", "fc00::/7",
# "2001:db8::/32", "ff00::/8", "fec0::/10"]
#
#ip_range_denylist =
# Optional IP address or network interface-name to bind as the source of
# URL preview requests. If not set, it will not bind to a specific
# address or interface.
#
# Interface names only supported on Linux, Android, and Fuchsia platforms;
# all other platforms can specify the IP address. To list the interfaces
# on your system, use the command `ip link show`.
#
# example: `"eth0"` or `"1.2.3.4"`
#
#url_preview_bound_interface =
# Vector list of domains allowed to send requests to for URL previews.
#
# This is a *contains* match, not an explicit match. Putting "google.com"
# will match "https://google.com" and
# "http://mymaliciousdomainexamplegoogle.com" Setting this to "*" will
# allow all URL previews. Please note that this opens up significant
# attack surface to your server, you are expected to be aware of the risks
# by doing so.
#
#url_preview_domain_contains_allowlist = []
# Vector list of explicit domains allowed to send requests to for URL
# previews.
#
# This is an *explicit* match, not a contains match. Putting "google.com"
# will match "https://google.com", "http://google.com", but not
# "https://mymaliciousdomainexamplegoogle.com". Setting this to "*" will
# allow all URL previews. Please note that this opens up significant
# attack surface to your server, you are expected to be aware of the risks
# by doing so.
#
#url_preview_domain_explicit_allowlist = []
# Vector list of explicit domains not allowed to send requests to for URL
# previews.
#
# This is an *explicit* match, not a contains match. Putting "google.com"
# will match "https://google.com", "http://google.com", but not
# "https://mymaliciousdomainexamplegoogle.com". The denylist is checked
# first before allowlist. Setting this to "*" will not do anything.
#
#url_preview_domain_explicit_denylist = []
# Vector list of URLs allowed to send requests to for URL previews.
#
# Note that this is a *contains* match, not an explicit match. Putting
# "google.com" will match "https://google.com/",
# "https://google.com/url?q=https://mymaliciousdomainexample.com", and
# "https://mymaliciousdomainexample.com/hi/google.com" Setting this to "*"
# will allow all URL previews. Please note that this opens up significant
# attack surface to your server, you are expected to be aware of the risks
# by doing so.
#
#url_preview_url_contains_allowlist = []
# Maximum amount of bytes allowed in a URL preview body size when
# spidering. Defaults to 256KB in bytes.
#
#url_preview_max_spider_size = 256000
# Option to decide whether you would like to run the domain allowlist
# checks (contains and explicit) on the root domain or not. Does not apply
# to URL contains allowlist. Defaults to false.
#
# Example usecase: If this is enabled and you have "wikipedia.org" allowed
# in the explicit and/or contains domain allowlist, it will allow all
# subdomains under "wikipedia.org" such as "en.m.wikipedia.org" as the
# root domain is checked and matched. Useful if the domain contains
# allowlist is still too broad for you but you still want to allow all the
# subdomains under a root domain.
#
#url_preview_check_root_domain = false
# List of forbidden room aliases and room IDs as strings of regex
# patterns.
#
# Regex can be used or explicit contains matches can be done by just
# specifying the words (see example).
#
# This is checked upon room alias creation, custom room ID creation if
# used, and startup as warnings if any room aliases in your database have
# a forbidden room alias/ID.
#
# example: ["19dollarfortnitecards", "b[4a]droom"]
#
#forbidden_alias_names = []
# List of forbidden username patterns/strings.
#
# Regex can be used or explicit contains matches can be done by just
# specifying the words (see example).
#
# This is checked upon username availability check, registration, and
# startup as warnings if any local users in your database have a forbidden
# username.
#
# example: ["administrator", "b[a4]dusernam[3e]"]
#
#forbidden_usernames = []
# Retry failed and incomplete messages to remote servers immediately upon
# startup. This is called bursting. If this is disabled, said messages may
# not be delivered until more messages are queued for that server. Do not
# change this option unless server resources are extremely limited or the
# scale of the server's deployment is huge. Do not disable this unless you
# know what you are doing.
#
#startup_netburst = true
# Messages are dropped and not reattempted. The `startup_netburst` option
# must be enabled for this value to have any effect. Do not change this
# value unless you know what you are doing. Set this value to -1 to
# reattempt every message without trimming the queues; this may consume
# significant disk. Set this value to 0 to drop all messages without any
# attempt at redelivery.
#
#startup_netburst_keep = 50
# Block non-admin local users from sending room invites (local and
# remote), and block non-admin users from receiving remote room invites.
#
# Admins are always allowed to send and receive all room invites.
#
#block_non_admin_invites = false
# Allow admins to enter commands in rooms other than "#admins" (admin
# room) by prefixing your message with "\!admin" or "\\!admin" followed up
# a normal conduwuit admin command. The reply will be publicly visible to
# the room, originating from the sender.
#
# example: \\!admin debug ping puppygock.gay
#
#admin_escape_commands = true
# Automatically activate the conduwuit admin room console / CLI on
# startup. This option can also be enabled with `--console` conduwuit
# argument.
#
#admin_console_automatic = false
# List of admin commands to execute on startup.
#
# This option can also be configured with the `--execute` conduwuit
# argument and can take standard shell commands and environment variables
#
# For example: `./conduwuit --execute "server admin-notice conduwuit has
# started up at $(date)"`
#
# example: admin_execute = ["debug ping puppygock.gay", "debug echo hi"]`
#
#admin_execute = []
# Ignore errors in startup commands.
#
# If false, conduwuit will error and fail to start if an admin execute
# command (`--execute` / `admin_execute`) fails.
#
#admin_execute_errors_ignore = false
# List of admin commands to execute on SIGUSR2.
#
# Similar to admin_execute, but these commands are executed when the
# server receives SIGUSR2 on supporting platforms.
#
#admin_signal_execute = []
# Controls the max log level for admin command log captures (logs
# generated from running admin commands). Defaults to "info" on release
# builds, else "debug" on debug builds.
#
#admin_log_capture = "info"
# The default room tag to apply on the admin room.
#
# On some clients like Element, the room tag "m.server_notice" is a
# special pinned room at the very bottom of your room list. The conduwuit
# admin room can be pinned here so you always have an easy-to-access
# shortcut dedicated to your admin room.
#
#admin_room_tag = "m.server_notice"
# Sentry.io crash/panic reporting, performance monitoring/metrics, etc.
# This is NOT enabled by default. conduwuit's default Sentry reporting
# endpoint domain is `o4506996327251968.ingest.us.sentry.io`.
#
#sentry = false
# Sentry reporting URL, if a custom one is desired.
#
#sentry_endpoint = "https://fe2eb4536aa04949e28eff3128d64757@o4506996327251968.ingest.us.sentry.io/4506996334657536"
# Report your conduwuit server_name in Sentry.io crash reports and
# metrics.
#
#sentry_send_server_name = false
# Performance monitoring/tracing sample rate for Sentry.io.
#
# Note that too high values may impact performance, and can be disabled by
# setting it to 0.0 (0%) This value is read as a percentage to Sentry,
# represented as a decimal. Defaults to 15% of traces (0.15)
#
#sentry_traces_sample_rate = 0.15
# Whether to attach a stacktrace to Sentry reports.
#
#sentry_attach_stacktrace = false
# Send panics to Sentry. This is true by default, but Sentry has to be
# enabled. The global `sentry` config option must be enabled to send any
# data.
#
#sentry_send_panic = true
# Send errors to sentry. This is true by default, but sentry has to be
# enabled. This option is only effective in release-mode; forced to false
# in debug-mode.
#
#sentry_send_error = true
# Controls the tracing log level for Sentry to send things like
# breadcrumbs and transactions
#
#sentry_filter = "info"
# Enable the tokio-console. This option is only relevant to developers.
#
# For more information, see:
# https://conduwuit.puppyirl.gay/development.html#debugging-with-tokio-console
#
#tokio_console = false
# This item is undocumented. Please contribute documentation for it.
#
#test = false
# Controls whether admin room notices like account registrations, password
# changes, account deactivations, room directory publications, etc will be
# sent to the admin room. Update notices and normal admin command
# responses will still be sent.
#
#admin_room_notices = true
# Enable database pool affinity support. On supporting systems, block
# device queue topologies are detected and the request pool is optimized
# for the hardware; db_pool_workers is determined automatically.
#
#db_pool_affinity = true
# Sets the number of worker threads in the frontend-pool of the database.
# This number should reflect the I/O capabilities of the system,
# such as the queue-depth or the number of simultaneous requests in
# flight. Defaults to 32 or four times the number of CPU cores, whichever
# is greater.
#
# Note: This value is only used if db_pool_affinity is disabled or not
# detected on the system, otherwise it is determined automatically.
#
#db_pool_workers = 32
# When db_pool_affinity is enabled and detected, the size of any worker
# group will not exceed the determined value. This is necessary when
# thread-pooling approach does not scale to the full capabilities of
# high-end hardware; using detected values without limitation could
# degrade performance.
#
# The value is multiplied by the number of cores which share a device
# queue, since group workers can be scheduled on any of those cores.
#
#db_pool_workers_limit = 64
# Determines the size of the queues feeding the database's frontend-pool.
# The size of the queue is determined by multiplying this value with the
# number of pool workers. When this queue is full, tokio tasks conducting
# requests will yield until space is available; this is good for
# flow-control by avoiding buffer-bloat, but can inhibit throughput if
# too low.
#
#db_pool_queue_mult = 4
# Sets the initial value for the concurrency of streams. This value simply
# allows overriding the default in the code. The default is 32, which is
# the same as the default in the code. Note this value is itself
# overridden by the computed stream_width_scale, unless that is disabled;
# this value can serve as a fixed-width instead.
#
#stream_width_default = 32
# Scales the stream width starting from a base value detected for the
# specific system. The base value is the database pool worker count
# determined from the hardware queue size (e.g. 32 for SSD or 64 or 128+
# for NVMe). This float allows scaling the width up or down by multiplying
# it (e.g. 1.5, 2.0, etc). The maximum result can be the size of the pool
# queue (see: db_pool_queue_mult) as any larger value will stall the tokio
# task. The value can also be scaled down (e.g. 0.5) to improve
# responsiveness for many users at the cost of throughput for each.
#
# Setting this value to 0.0 causes the stream width to be fixed at the
# value of stream_width_default. The default scale is 1.0 to match the
# capabilities detected for the system.
#
#stream_width_scale = 1.0
# Sets the initial amplification factor. This controls batch sizes of
# requests made by each pool worker, multiplying the throughput of each
# stream. This value is somewhat abstract from specific hardware
# characteristics and can be significantly larger than any thread count or
# queue size. This is because each database query may require several
# index lookups, thus many database queries in a batch may make progress
# independently while also sharing index and data blocks which may or may
# not be cached. It is worthwhile to submit huge batches to reduce
# complexity. The maximum value is 32768, though sufficient hardware is
# still advised for that.
#
#stream_amplification = 1024
# Number of sender task workers; determines sender parallelism. Default is
# '0' which means the value is determined internally, likely matching the
# number of tokio worker-threads or number of cores, etc. Override by
# setting a non-zero value.
#
#sender_workers = 0
# Enables listener sockets; can be set to false to disable listening. This
# option is intended for developer/diagnostic purposes only.
#
#listening = true
# Enables configuration reload when the server receives SIGUSR1 on
# supporting platforms.
#
#config_reload_signal = true
[global.tls]
# Path to a valid TLS certificate file.
#
# example: "/path/to/my/certificate.crt"
#
#certs =
# Path to a valid TLS certificate private key.
#
# example: "/path/to/my/certificate.key"
#
#key =
# Whether to listen and allow for HTTP and HTTPS connections (insecure!)
#
#dual_protocol = false
[global.well_known]
# The server URL that the client well-known file will serve. This should
# not contain a port, and should just be a valid HTTPS URL.
#
# example: "https://matrix.example.com"
#
#client =
# The server base domain of the URL with a specific port that the server
# well-known file will serve. This should contain a port at the end, and
# should not be a URL.
#
# example: "matrix.example.com:443"
#
#server =
# This item is undocumented. Please contribute documentation for it.
#
#support_page =
# This item is undocumented. Please contribute documentation for it.
#
#support_role =
# This item is undocumented. Please contribute documentation for it.
#
#support_email =
# This item is undocumented. Please contribute documentation for it.
#
#support_mxid =
[global.blurhashing]
# blurhashing x component, 4 is recommended by https://blurha.sh/
#
#components_x = 4
# blurhashing y component, 3 is recommended by https://blurha.sh/
#
#components_y = 3
# Max raw size that the server will blurhash, this is the size of the
# image after converting it to raw data, it should be higher than the
# upload limit but not too high. The higher it is the higher the
# potential load will be for clients requesting blurhashes. The default
# is 33.55MB. Setting it to 0 disables blurhashing.
#
#blurhash_max_raw_size = 33554432
Debian systemd unit file
Debian systemd unit file
[Unit]
Description=conduwuit Matrix homeserver
Wants=network-online.target
After=network-online.target
Alias=matrix-conduwuit.service
Documentation=https://conduwuit.puppyirl.gay/
[Service]
DynamicUser=yes
User=conduwuit
Group=conduwuit
Type=notify
Environment="CONDUWUIT_CONFIG=/etc/conduwuit/conduwuit.toml"
ExecStart=/usr/sbin/conduwuit
ReadWritePaths=/var/lib/conduwuit /etc/conduwuit
AmbientCapabilities=
CapabilityBoundingSet=
DevicePolicy=closed
LockPersonality=yes
MemoryDenyWriteExecute=yes
NoNewPrivileges=yes
#ProcSubset=pid
ProtectClock=yes
ProtectControlGroups=yes
ProtectHome=yes
ProtectHostname=yes
ProtectKernelLogs=yes
ProtectKernelModules=yes
ProtectKernelTunables=yes
ProtectProc=invisible
ProtectSystem=strict
PrivateDevices=yes
PrivateMounts=yes
PrivateTmp=yes
PrivateUsers=yes
PrivateIPC=yes
RemoveIPC=yes
RestrictAddressFamilies=AF_INET AF_INET6 AF_UNIX
RestrictNamespaces=yes
RestrictRealtime=yes
RestrictSUIDSGID=yes
SystemCallArchitectures=native
SystemCallFilter=@system-service @resources
SystemCallFilter=~@clock @debug @module @mount @reboot @swap @cpu-emulation @obsolete @timer @chown @setuid @privileged @keyring @ipc
SystemCallErrorNumber=EPERM
#StateDirectory=conduwuit
RuntimeDirectory=conduwuit
RuntimeDirectoryMode=0750
Restart=on-failure
RestartSec=5
TimeoutStopSec=2m
TimeoutStartSec=2m
StartLimitInterval=1m
StartLimitBurst=5
[Install]
WantedBy=multi-user.target
Arch Linux systemd unit file
Arch Linux systemd unit file
[Unit]
Description=conduwuit Matrix homeserver
Wants=network-online.target
After=network-online.target
Documentation=https://conduwuit.puppyirl.gay/
RequiresMountsFor=/var/lib/private/conduwuit
Alias=matrix-conduwuit.service
[Service]
DynamicUser=yes
Type=notify-reload
ReloadSignal=SIGUSR1
TTYPath=/dev/tty25
DeviceAllow=char-tty
StandardInput=tty-force
StandardOutput=tty
StandardError=journal+console
TTYReset=yes
# uncomment to allow buffer to be cleared every restart
TTYVTDisallocate=no
TTYColumns=120
TTYRows=40
AmbientCapabilities=
CapabilityBoundingSet=
DevicePolicy=closed
LockPersonality=yes
MemoryDenyWriteExecute=yes
NoNewPrivileges=yes
#ProcSubset=pid
ProtectClock=yes
ProtectControlGroups=yes
ProtectHome=yes
ProtectHostname=yes
ProtectKernelLogs=yes
ProtectKernelModules=yes
ProtectKernelTunables=yes
ProtectProc=invisible
ProtectSystem=strict
PrivateDevices=yes
PrivateMounts=yes
PrivateTmp=yes
PrivateUsers=yes
PrivateIPC=yes
RemoveIPC=yes
RestrictAddressFamilies=AF_INET AF_INET6 AF_UNIX
RestrictNamespaces=yes
RestrictRealtime=yes
RestrictSUIDSGID=yes
SystemCallArchitectures=native
SystemCallFilter=@system-service @resources
SystemCallFilter=~@clock @debug @module @mount @reboot @swap @cpu-emulation @obsolete @timer @chown @setuid @privileged @keyring @ipc
SystemCallErrorNumber=EPERM
StateDirectory=conduwuit
RuntimeDirectory=conduwuit
RuntimeDirectoryMode=0750
Environment="CONDUWUIT_CONFIG=/etc/conduwuit/conduwuit.toml"
BindPaths=/var/lib/private/conduwuit:/var/lib/matrix-conduit
BindPaths=/var/lib/private/conduwuit:/var/lib/private/matrix-conduit
ExecStart=/usr/bin/conduwuit
Restart=on-failure
RestartSec=5
TimeoutStopSec=4m
TimeoutStartSec=4m
StartLimitInterval=1m
StartLimitBurst=5
[Install]
WantedBy=multi-user.target
Deploying
This chapter describes various ways to deploy conduwuit.
Generic deployment documentation
Getting help
If you run into any problems while setting up conduwuit, ask us in
#conduwuit:puppygock.gayor open an issue on GitHub.
Installing conduwuit
Static prebuilt binary
You may simply download the binary that fits your machine architecture (x86_64
or aarch64). Run uname -m to see what you need.
Prebuilt fully static musl binaries can be downloaded from the latest tagged
release here or
main CI branch workflow artifact output. These also include Debian/Ubuntu
packages.
Binaries are also available on my website directly at: https://pup.systems/~strawberry/conduwuit/
These can be curl'd directly from. ci-bins are CI workflow binaries by commit
hash/revision, and releases are tagged releases. Sort by descending last
modified for the latest.
These binaries have jemalloc and io_uring statically linked and included with them, so no additional dynamic dependencies need to be installed.
For the best performance; if using an x86_64 CPU made in the last ~15 years,
we recommend using the -haswell- optimised binaries. This sets
-march=haswell which is the most compatible and highest performance with
optimised binaries. The database backend, RocksDB, most benefits from this as it
will then use hardware accelerated CRC32 hashing/checksumming which is critical
for performance.
Compiling
Alternatively, you may compile the binary yourself. We recommend using Nix (or Lix) to build conduwuit as this has the most guaranteed reproducibiltiy and easiest to get a build environment and output going. This also allows easy cross-compilation.
You can run the nix build -L .#static-x86_64-linux-musl-all-features or
nix build -L .#static-aarch64-linux-musl-all-features commands based
on architecture to cross-compile the necessary static binary located at
result/bin/conduwuit. This is reproducible with the static binaries produced
in our CI.
If wanting to build using standard Rust toolchains, make sure you install:
liburing-devon the compiling machine, andliburingon the target host- LLVM and libclang for RocksDB
You can build conduwuit using cargo build --release --all-features
Adding a conduwuit user
While conduwuit can run as any user it is better to use dedicated users for different services. This also allows you to make sure that the file permissions are correctly set up.
In Debian, you can use this command to create a conduwuit user:
sudo adduser --system conduwuit --group --disabled-login --no-create-home
For distros without adduser (or where it's a symlink to useradd):
sudo useradd -r --shell /usr/bin/nologin --no-create-home conduwuit
Forwarding ports in the firewall or the router
Matrix's default federation port is port 8448, and clients must be using port 443.
If you would like to use only port 443, or a different port, you will need to setup
delegation. conduwuit has config options for doing delegation, or you can configure
your reverse proxy to manually serve the necessary JSON files to do delegation
(see the [global.well_known] config section).
If conduwuit runs behind a router or in a container and has a different public IP address than the host system these public ports need to be forwarded directly or indirectly to the port mentioned in the config.
Note for NAT users; if you have trouble connecting to your server from the inside of your network, you need to research your router and see if it supports "NAT hairpinning" or "NAT loopback".
If your router does not support this feature, you need to research doing local
DNS overrides and force your Matrix DNS records to use your local IP internally.
This can be done at the host level using /etc/hosts. If you need this to be
on the network level, consider something like NextDNS or Pi-Hole.
Setting up a systemd service
Two example systemd units for conduwuit can be found
on the configuration page.
You may need to change the ExecStart= path to where you placed the conduwuit
binary if it is not /usr/bin/conduwuit.
On systems where rsyslog is used alongside journald (i.e. Red Hat-based distros
and OpenSUSE), put $EscapeControlCharactersOnReceive off inside
/etc/rsyslog.conf to allow color in logs.
If you are using a different database_path other than the systemd unit
configured default /var/lib/conduwuit, you need to add your path to the
systemd unit's ReadWritePaths=. This can be done by either directly editing
conduwuit.service and reloading systemd, or running systemctl edit conduwuit.service
and entering the following:
[Service]
ReadWritePaths=/path/to/custom/database/path
Creating the conduwuit configuration file
Now we need to create the conduwuit's config file in
/etc/conduwuit/conduwuit.toml. The example config can be found at
conduwuit-example.toml.
Please take a moment to read the config. You need to change at least the server name.
RocksDB is the only supported database backend.
Setting the correct file permissions
If you are using a dedicated user for conduwuit, you will need to allow it to read the config. To do that you can run this:
sudo chown -R root:root /etc/conduwuit
sudo chmod -R 755 /etc/conduwuit
If you use the default database path you also need to run this:
sudo mkdir -p /var/lib/conduwuit/
sudo chown -R conduwuit:conduwuit /var/lib/conduwuit/
sudo chmod 700 /var/lib/conduwuit/
Setting up the Reverse Proxy
We recommend Caddy as a reverse proxy, as it is trivial to use, handling TLS certificates, reverse proxy headers, etc transparently with proper defaults. For other software, please refer to their respective documentation or online guides.
Caddy
After installing Caddy via your preferred method, create /etc/caddy/conf.d/conduwuit_caddyfile
and enter this (substitute for your server name).
your.server.name, your.server.name:8448 {
# TCP reverse_proxy
reverse_proxy 127.0.0.1:6167
# UNIX socket
#reverse_proxy unix//run/conduwuit/conduwuit.sock
}
That's it! Just start and enable the service and you're set.
sudo systemctl enable --now caddy
Other Reverse Proxies
As we would prefer our users to use Caddy, we will not provide configuration files for other proxys.
You will need to reverse proxy everything under following routes:
/_matrix/- core Matrix C-S and S-S APIs/_conduwuit/- ad-hoc conduwuit routes such as/local_user_countand/server_version
You can optionally reverse proxy the following individual routes:
/.well-known/matrix/clientand/.well-known/matrix/serverif using conduwuit to perform delegation (see the[global.well_known]config section)/.well-known/matrix/supportif using conduwuit to send the homeserver admin contact and support page (formerly known as MSC1929)/if you would like to seehewwo from conduwuit woof!at the root
See the following spec pages for more details on these files:
Examples of delegation:
For Apache and Nginx there are many examples available online.
Lighttpd is not supported as it seems to mess with the X-Matrix Authorization
header, making federation non-functional. If a workaround is found, feel free to share to get it added to the documentation here.
If using Apache, you need to use nocanon in your ProxyPass directive to prevent httpd from messing with the X-Matrix header (note that Apache isn't very good as a general reverse proxy and we discourage the usage of it if you can).
If using Nginx, you need to give conduwuit the request URI using $request_uri, or like so:
proxy_pass http://127.0.0.1:6167$request_uri;proxy_pass http://127.0.0.1:6167;
Nginx users need to increase client_max_body_size (default is 1M) to match
max_request_size defined in conduwuit.toml.
You're done
Now you can start conduwuit with:
sudo systemctl start conduwuit
Set it to start automatically when your system boots with:
sudo systemctl enable conduwuit
How do I know it works?
You can open a Matrix client, enter your homeserver and try to register.
You can also use these commands as a quick health check (replace
your.server.name).
curl https://your.server.name/_conduwuit/server_version
# If using port 8448
curl https://your.server.name:8448/_conduwuit/server_version
# If federation is enabled
curl https://your.server.name:8448/_matrix/federation/v1/version
- To check if your server can talk with other homeservers, you can use the Matrix Federation Tester. If you can register but cannot join federated rooms check your config again and also check if the port 8448 is open and forwarded correctly.
What's next?
Audio/Video calls
For Audio/Video call functionality see the TURN Guide.
Appservices
If you want to set up an appservice, take a look at the Appservice Guide.
conduwuit for NixOS
conduwuit can be acquired by Nix (or Lix) from various places:
- The
flake.nixat the root of the repo - The
default.nixat the root of the repo - From conduwuit's binary cache
A community maintained NixOS package is available at conduwuit
Binary cache
A binary cache for conduwuit that the CI/CD publishes to is available at the following places (both are the same just different names):
https://attic.kennel.juneis.dog/conduit
conduit:eEKoUwlQGDdYmAI/Q/0slVlegqh/QmAvQd7HBSm21Wk=
https://attic.kennel.juneis.dog/conduwuit
conduwuit:BbycGUgTISsltcmH0qNjFR9dbrQNYgdIAcmViSGoVTE=
The binary caches were recreated some months ago due to attic issues. The old public keys were:
conduit:Isq8FGyEC6FOXH6nD+BOeAA+bKp6X6UIbupSlGEPuOg=
conduwuit:lYPVh7o1hLu1idH4Xt2QHaRa49WRGSAqzcfFd94aOTw=
If needed, we have a binary cache on Cachix but it is only limited to 5GB:
https://conduwuit.cachix.org
conduwuit.cachix.org-1:MFRm6jcnfTf0jSAbmvLfhO3KBMt4px+1xaereWXp8Xg=
If specifying a Git remote URL in your flake, you can use any remotes that
are specified on the README (the mirrors), such as the GitHub: github:girlbossceo/conduwuit
NixOS module
The flake.nix and default.nix do not currently provide a NixOS module (contributions
welcome!), so services.matrix-conduit from Nixpkgs can be used to configure
conduwuit.
Conduit NixOS Config Module and SQLite
Beware! The services.matrix-conduit module defaults to SQLite as a database backend.
Conduwuit dropped SQLite support in favor of exclusively supporting the much faster RocksDB.
Make sure that you are using the RocksDB backend before migrating!
There is a tool to migrate a Conduit SQLite database to RocksDB.
If you want to run the latest code, you should get conduwuit from the flake.nix
or default.nix and set services.matrix-conduit.package
appropriately to use conduwuit instead of Conduit.
UNIX sockets
Due to the lack of a conduwuit NixOS module, when using the services.matrix-conduit module
a workaround like the one below is necessary to use UNIX sockets. This is because the UNIX
socket option does not exist in Conduit, and the module forcibly sets the address and
port config options.
options.services.matrix-conduit.settings = lib.mkOption {
apply = old: old // (
if (old.global ? "unix_socket_path")
then { global = builtins.removeAttrs old.global [ "address" "port" ]; }
else { }
);
};
Additionally, the matrix-conduit systemd unit in the module does not allow
the AF_UNIX socket address family in their systemd unit's RestrictAddressFamilies= which
disallows the namespace from accessing or creating UNIX sockets and has to be enabled like so:
systemd.services.conduit.serviceConfig.RestrictAddressFamilies = [ "AF_UNIX" ];
Even though those workarounds are feasible a conduwuit NixOS configuration module, developed and published by the community, would be appreciated.
jemalloc and hardened profile
conduwuit uses jemalloc by default. This may interfere with the hardened.nix profile
due to them using scudo by default. You must either disable/hide scudo from conduwuit, or
disable jemalloc like so:
let
conduwuit = pkgs.unstable.conduwuit.override {
enableJemalloc = false;
};
in
conduwuit for Docker
Docker
To run conduwuit with Docker you can either build the image yourself or pull it from a registry.
Use a registry
OCI images for conduwuit are available in the registries listed below.
| Registry | Image | Size | Notes |
|---|---|---|---|
| GitHub Registry | ghcr.io/girlbossceo/conduwuit:latest |  | Stable latest tagged image. |
| GitLab Registry | registry.gitlab.com/conduwuit/conduwuit:latest |  | Stable latest tagged image. |
| Docker Hub | docker.io/girlbossceo/conduwuit:latest |  | Stable latest tagged image. |
| GitHub Registry | ghcr.io/girlbossceo/conduwuit:main |  | Stable main branch. |
| GitLab Registry | registry.gitlab.com/conduwuit/conduwuit:main |  | Stable main branch. |
| Docker Hub | docker.io/girlbossceo/conduwuit:main |  | Stable main branch. |
OCI image .tar.gz files are also hosted directly at when uploaded by CI with a
commit hash/revision or a tagged release: https://pup.systems/~strawberry/conduwuit/
Use
docker image pull $LINK
to pull it to your machine.
Run
When you have the image you can simply run it with
docker run -d -p 8448:6167 \
-v db:/var/lib/conduwuit/ \
-e CONDUWUIT_SERVER_NAME="your.server.name" \
-e CONDUWUIT_ALLOW_REGISTRATION=false \
--name conduwuit $LINK
or you can use docker compose.
The -d flag lets the container run in detached mode. You may supply an
optional conduwuit.toml config file, the example config can be found
here. You can pass in different env vars to
change config values on the fly. You can even configure conduwuit completely by
using env vars. For an overview of possible values, please take a look at the
docker-compose.yml file.
If you just want to test conduwuit for a short time, you can use the --rm
flag, which will clean up everything related to your container after you stop
it.
Docker-compose
If the docker run command is not for you or your setup, you can also use one
of the provided docker-compose files.
Depending on your proxy setup, you can use one of the following files;
- If you already have a
traefikinstance set up, usedocker-compose.for-traefik.yml - If you don't have a
traefikinstance set up and would like to use it, usedocker-compose.with-traefik.yml - If you want a setup that works out of the box with
caddy-docker-proxy, usedocker-compose.with-caddy.ymland replace allexample.complaceholders with your own domain - For any other reverse proxy, use
docker-compose.yml
When picking the traefik-related compose file, rename it so it matches
docker-compose.yml, and rename the override file to
docker-compose.override.yml. Edit the latter with the values you want for your
server.
When picking the caddy-docker-proxy compose file, it's important to first
create the caddy network before spinning up the containers:
docker network create caddy
After that, you can rename it so it matches docker-compose.yml and spin up the
containers!
Additional info about deploying conduwuit can be found here.
Build
Official conduwuit images are built using Nix's
buildLayeredImage. This ensures all OCI images are
repeatable and reproducible by anyone, keeps the images lightweight, and can be
built offline.
This also ensures portability of our images because buildLayeredImage builds
OCI images, not Docker images, and works with other container software.
The OCI images are OS-less with only a very minimal environment of the tini
init system, CA certificates, and the conduwuit binary. This does mean there is
not a shell, but in theory you can get a shell by adding the necessary layers
to the layered image. However it's very unlikely you will need a shell for any
real troubleshooting.
The flake file for the OCI image definition is at nix/pkgs/oci-image/default.nix.
To build an OCI image using Nix, the following outputs can be built:
nix build -L .#oci-image(default features, x86_64 glibc)nix build -L .#oci-image-x86_64-linux-musl(default features, x86_64 musl)nix build -L .#oci-image-aarch64-linux-musl(default features, aarch64 musl)nix build -L .#oci-image-x86_64-linux-musl-all-features(all features, x86_64 musl)nix build -L .#oci-image-aarch64-linux-musl-all-features(all features, aarch64 musl)
Run
If you already have built the image or want to use one from the registries, you can just start the container and everything else in the compose file in detached mode with:
docker compose up -d
Note: Don't forget to modify and adjust the compose file to your needs.
Use Traefik as Proxy
As a container user, you probably know about Traefik. It is a easy to use
reverse proxy for making containerized app and services available through the
web. With the two provided files,
docker-compose.for-traefik.yml (or
docker-compose.with-traefik.yml) and
docker-compose.override.yml, it is equally easy
to deploy and use conduwuit, with a little caveat. If you already took a look at
the files, then you should have seen the well-known service, and that is the
little caveat. Traefik is simply a proxy and loadbalancer and is not able to
serve any kind of content, but for conduwuit to federate, we need to either
expose ports 443 and 8448 or serve two endpoints .well-known/matrix/client
and .well-known/matrix/server.
With the service well-known we use a single nginx container that will serve
those two files.
Voice communication
See the TURN page.
conduwuit for Kubernetes
conduwuit doesn't support horizontal scalability or distributed loading natively, however a community maintained Helm Chart is available here to run conduwuit on Kubernetes: https://gitlab.cronce.io/charts/conduwuit
Should changes need to be made, please reach out to the maintainer in our Matrix room as this is not maintained/controlled by the conduwuit maintainers.
conduwuit for Arch Linux
Currently conduwuit is only on the Arch User Repository (AUR).
The conduwuit AUR packages are community maintained and are not maintained by conduwuit development team, but the AUR package maintainers are in the Matrix room. Please attempt to verify your AUR package's PKGBUILD file looks fine before asking for support.
- conduwuit - latest tagged conduwuit
- conduwuit-git - latest git
conduwuit from
mainbranch - conduwuit-bin - latest tagged conduwuit static binary
conduwuit for Debian
Information about downloading and deploying the Debian package. This may also be
referenced for other apt-based distros such as Ubuntu.
Installation
It is recommended to see the generic deployment guide for further information if needed as usage of the Debian package is generally related.
No apt repository is currently offered yet, it is in the works/development.
Configuration
When installed, the example config is placed at /etc/conduwuit/conduwuit.toml
as the default config. The config mentions things required to be changed before
starting.
You can tweak more detailed settings by uncommenting and setting the config
options in /etc/conduwuit/conduwuit.toml.
Running
The package uses the conduwuit.service systemd unit file to start and stop conduwuit. The binary is installed at /usr/sbin/conduwuit.
This package assumes by default that conduwuit will be placed behind a reverse proxy. The default config options apply (listening on localhost and TCP port 6167). Matrix federation requires a valid domain name and TLS, so you will need to set up TLS certificates and renewal for it to work properly if you intend to federate.
Consult various online documentation and guides on setting up a reverse proxy and TLS. Caddy is documented at the generic deployment guide as it's the easiest and most user friendly.
conduwuit for FreeBSD
conduwuit at the moment does not provide FreeBSD builds or have FreeBSD packaging, however conduwuit does build and work on FreeBSD using the system-provided RocksDB.
Contributions for getting conduwuit packaged are welcome.
Setting up TURN/STURN
In order to make or receive calls, a TURN server is required. conduwuit suggests using Coturn for this purpose, which is also available as a Docker image.
Configuration
Create a configuration file called coturn.conf containing:
use-auth-secret
static-auth-secret=<a secret key>
realm=<your server domain>
A common way to generate a suitable alphanumeric secret key is by using pwgen -s 64 1.
These same values need to be set in conduwuit. See the example config in the TURN section for configuring these and restart conduwuit after.
turn_secret or a path to turn_secret_file must have a value of your
coturn static-auth-secret, or use turn_username and turn_password
if using legacy username:password TURN authentication (not preferred).
turn_uris must be the list of TURN URIs you would like to send to the client.
Typically you will just replace the example domain example.turn.uri with the
realm you set from the example config.
If you are using TURN over TLS, you can replace turn: with turns: in the
turn_uris config option to instruct clients to attempt to connect to
TURN over TLS. This is highly recommended.
If you need unauthenticated access to the TURN URIs, or some clients may be
having trouble, you can enable turn_guest_access in conduwuit which disables
authentication for the TURN URI endpoint /_matrix/client/v3/voip/turnServer
Run
Run the Coturn image using
docker run -d --network=host -v
$(pwd)/coturn.conf:/etc/coturn/turnserver.conf coturn/coturn
or docker-compose. For the latter, paste the following section into a file
called docker-compose.yml and run docker compose up -d in the same
directory.
version: 3
services:
turn:
container_name: coturn-server
image: docker.io/coturn/coturn
restart: unless-stopped
network_mode: "host"
volumes:
- ./coturn.conf:/etc/coturn/turnserver.conf
To understand why the host networking mode is used and explore alternative configuration options, please visit Coturn's Docker documentation.
For security recommendations see Synapse's Coturn documentation.
Setting up Appservices
Getting help
If you run into any problems while setting up an Appservice: ask us in #conduwuit:puppygock.gay or open an issue on GitHub.
Set up the appservice - general instructions
Follow whatever instructions are given by the appservice. This usually includes downloading, changing its config (setting domain, homeserver url, port etc.) and later starting it.
At some point the appservice guide should ask you to add a registration yaml file to the homeserver. In Synapse you would do this by adding the path to the homeserver.yaml, but in conduwuit you can do this from within Matrix:
First, go into the #admins room of your homeserver. The first person that
registered on the homeserver automatically joins it. Then send a message into
the room like this:
!admin appservices register
```
paste
the
contents
of
the
yaml
registration
here
```
You can confirm it worked by sending a message like this:
!admin appservices list
The server bot should answer with Appservices (1): your-bridge
Then you are done. conduwuit will send messages to the appservices and the appservice can send requests to the homeserver. You don't need to restart conduwuit, but if it doesn't work, restarting while the appservice is running could help.
Appservice-specific instructions
Remove an appservice
To remove an appservice go to your admin room and execute
!admin appservices unregister <name>
where <name> one of the output of appservices list.
Maintaining your conduwuit setup
Moderation
conduwuit has moderation through admin room commands. "binary commands" (medium priority) and an admin API (low priority) is planned. Some moderation-related config options are available in the example config such as "global ACLs" and blocking media requests to certain servers. See the example config for the moderation config options under the "Moderation / Privacy / Security" section.
conduwuit has moderation admin commands for:
- managing room aliases (
!admin rooms alias) - managing room directory (
!admin rooms directory) - managing room banning/blocking and user removal (
!admin rooms moderation) - managing user accounts (
!admin users) - fetching
/.well-known/matrix/supportfrom servers (!admin federation) - blocking incoming federation for certain rooms (not the same as room banning)
(
!admin federation) - deleting media (see the media section)
Any commands with -list in them will require a codeblock in the message with
each object being newline delimited. An example of doing this is:
!admin rooms moderation ban-list-of-rooms
```
!roomid1:server.name
#badroomalias1:server.name
!roomid2:server.name
!roomid3:server.name
#badroomalias2:server.name
```
Database (RocksDB)
Generally there is very little you need to do. Compaction is ran automatically based on various defined thresholds tuned for conduwuit to be high performance with the least I/O amplifcation or overhead. Manually running compaction is not recommended, or compaction via a timer, due to creating unnecessary I/O amplification. RocksDB is built with io_uring support via liburing for improved read performance.
RocksDB troubleshooting can be found in the RocksDB section of troubleshooting.
Compression
Some RocksDB settings can be adjusted such as the compression method chosen. See the RocksDB section in the example config.
btrfs users have reported that database compression does not need to be disabled
on conduwuit as the filesystem already does not attempt to compress. This can be
validated by using filefrag -v on a .SST file in your database, and ensure
the physical_offset matches (no filesystem compression). It is very important
to ensure no additional filesystem compression takes place as this can render
unbuffered Direct IO inoperable, significantly slowing down read and write
performance. See https://btrfs.readthedocs.io/en/latest/Compression.html#compatibility
Compression is done using the COW mechanism so it’s incompatible with nodatacow. Direct IO read works on compressed files but will fall back to buffered writes and leads to no compression even if force compression is set. Currently nodatasum and compression don’t work together.
Files in database
Do not touch any of the files in the database directory. This must be said due
to users being mislead by the .log files in the RocksDB directory, thinking
they're server logs or database logs, however they are critical RocksDB files
related to WAL tracking.
The only safe files that can be deleted are the LOG files (all caps). These
are the real RocksDB telemetry/log files, however conduwuit has already
configured to only store up to 3 RocksDB LOG files due to generall being
useless for average users unless troubleshooting something low-level. If you
would like to store nearly none at all, see the rocksdb_max_log_files
config option.
Backups
Currently only RocksDB supports online backups. If you'd like to backup your
database online without any downtime, see the !admin server command for the
backup commands and the database_backup_path config options in the example
config. Please note that the format of the database backup is not the exact
same. This is unfortunately a bad design choice by Facebook as we are using the
database backup engine API from RocksDB, however the data is still there and can
still be joined together.
To restore a backup from an online RocksDB backup:
- shutdown conduwuit
- create a new directory for merging together the data
- in the online backup created, copy all
.sstfiles in$DATABASE_BACKUP_PATH/shared_checksumto your new directory - trim all the strings so instead of
######_sxxxxxxxxx.sst, it reads######.sst. A way of doing this with sed and bash isfor file in *.sst; do mv "$file" "$(echo "$file" | sed 's/_s.*/.sst/')"; done - copy all the files in
$DATABASE_BACKUP_PATH/1(or the latest backup number if you have multiple) to your new directory - set your
database_pathconfig option to your new directory, or replace your old one with the new one you crafted - start up conduwuit again and it should open as normal
If you'd like to do an offline backup, shutdown conduwuit and copy your
database_path directory elsewhere. This can be restored with no modifications
needed.
Backing up media is also just copying the media/ directory from your database
directory.
Media
Media still needs various work, however conduwuit implements media deletion via:
- MXC URI or Event ID (unencrypted and attempts to find the MXC URI in the event)
- Delete list of MXC URIs
- Delete remote media in the past
Nseconds/minutes via filesystem metadata on the file created time (btime) or file modified time (mtime)
See the !admin media command for further information. All media in conduwuit
is stored at $DATABASE_DIR/media. This will be configurable soon.
If you are finding yourself needing extensive granular control over media, we recommend looking into Matrix Media Repo. conduwuit intends to implement various utilities for media, but MMR is dedicated to extensive media management.
Built-in S3 support is also planned, but for now using a "S3 filesystem" on
media/ works. conduwuit also sends a Cache-Control header of 1 year and
immutable for all media requests (download and thumbnail) to reduce unnecessary
media requests from browsers, reduce bandwidth usage, and reduce load.
Troubleshooting conduwuit
Docker users ⚠️
Docker is extremely UX unfriendly. Because of this, a ton of issues or support is actually Docker support, not conduwuit support. We also cannot document the ever-growing list of Docker issues here.
If you intend on asking for support and you are using Docker, PLEASE triple validate your issues are NOT because you have a misconfiguration in your Docker setup.
If there are things like Compose file issues or Dockerhub image issues, those can still be mentioned as long as they're something we can fix.
conduwuit and Matrix issues
Lost access to admin room
You can reinvite yourself to the admin room through the following methods:
- Use the
--execute "users make_user_admin <username>"conduwuit binary argument once to invite yourslf to the admin room on startup - Use the conduwuit console/CLI to run the
users make_user_admincommand - Or specify the
emergency_passwordconfig option to allow you to temporarily log into the server account (@conduit) from a web client
General potential issues
Potential DNS issues when using Docker
Docker has issues with its default DNS setup that may cause DNS to not be properly functional when running conduwuit, resulting in federation issues. The symptoms of this have shown in excessively long room joins (30+ minutes) from very long DNS timeouts, log entries of "mismatching responding nameservers", and/or partial or non-functional inbound/outbound federation.
This is not a conduwuit issue, and is purely a Docker issue. It is not sustainable for heavy DNS activity which is normal for Matrix federation. The workarounds for this are:
- Use DNS over TCP via the config option
query_over_tcp_only = true - Don't use Docker's default DNS setup and instead allow the container to use
and communicate with your host's DNS servers (host's
/etc/resolv.conf)
DNS No connections available error message
If you receive spurious amounts of error logs saying "DNS No connections
available", this is due to your DNS server (servers from /etc/resolv.conf)
being overloaded and unable to handle typical Matrix federation volume. Some
users have reported that the upstream servers are rate-limiting them as well
when they get this error (e.g. popular upstreams like Google DNS).
Matrix federation is extremely heavy and sends wild amounts of DNS requests. Unfortunately this is by design and has only gotten worse with more server/destination resolution steps. Synapse also expects a very perfect DNS setup.
There are some ways you can reduce the amount of DNS queries, but ultimately the best solution/fix is selfhosting a high quality caching DNS server like Unbound without any upstream resolvers, and without DNSSEC validation enabled.
DNSSEC validation is highly recommended to be disabled due to DNSSEC being very computationally expensive, and is extremely susceptible to denial of service, especially on Matrix. Many servers also strangely have broken DNSSEC setups and will result in non-functional federation.
conduwuit cannot provide a "works-for-everyone" Unbound DNS setup guide, but
the official Unbound tuning guide and the Unbound Arch Linux wiki page
may be of interest. Disabling DNSSEC on Unbound is commenting out trust-anchors
config options and removing the validator module.
Avoid using systemd-resolved as it does not perform very well under
high load, and we have identified its DNS caching to not be very effective.
dnsmasq can possibly work, but it does not support TCP fallback which can be
problematic when receiving large DNS responses such as from large SRV records.
If you still want to use dnsmasq, make sure you disable dns_tcp_fallback
in conduwuit config.
Raising dns_cache_entries in conduwuit config from the default can also assist
in DNS caching, but a full-fledged external caching resolver is better and more
reliable.
If you don't have IPv6 connectivity, changing ip_lookup_strategy to match
your setup can help reduce unnecessary AAAA queries
(1 - Ipv4Only (Only query for A records, no AAAA/IPv6)).
If your DNS server supports it, some users have reported enabling
query_over_tcp_only to force only TCP querying by default has improved DNS
reliability at a slight performance cost due to TCP overhead.
RocksDB / database issues
Database corruption
If your database is corrupted and is failing to start (e.g. checksum mismatch), it may be recoverable but careful steps must be taken, and there is no guarantee it may be recoverable.
The first thing that can be done is launching conduwuit with the
rocksdb_repair config option set to true. This will tell RocksDB to attempt to
repair itself at launch. If this does not work, disable the option and continue
reading.
RocksDB has the following recovery modes:
TolerateCorruptedTailRecordsAbsoluteConsistencyPointInTimeSkipAnyCorruptedRecord
By default, conduwuit uses TolerateCorruptedTailRecords as generally these may
be due to bad federation and we can re-fetch the correct data over federation.
The RocksDB default is PointInTime which will attempt to restore a "snapshot"
of the data when it was last known to be good. This data can be either a few
seconds old, or multiple minutes prior. PointInTime may not be suitable for
default usage due to clients and servers possibly not being able to handle
sudden "backwards time travels", and AbsoluteConsistency may be too strict.
AbsoluteConsistency will fail to start the database if any sign of corruption
is detected. SkipAnyCorruptedRecord will skip all forms of corruption unless
it forbids the database from opening (e.g. too severe). Usage of
SkipAnyCorruptedRecord voids any support as this may cause more damage and/or
leave your database in a permanently inconsistent state, but it may do something
if PointInTime does not work as a last ditch effort.
With this in mind:
- First start conduwuit with the
PointInTimerecovery method. See the example config for how to do this usingrocksdb_recovery_mode - If your database successfully opens, clients are recommended to clear their client cache to account for the rollback
- Leave your conduwuit running in
PointInTimefor at least 30-60 minutes so as much possible corruption is restored - If all goes will, you should be able to restore back to using
TolerateCorruptedTailRecordsand you have successfully recovered your database
Debugging
Note that users should not really be debugging things. If you find yourself
debugging and find the issue, please let us know and/or how we can fix it.
Various debug commands can be found in !admin debug.
Debug/Trace log level
conduwuit builds without debug or trace log levels at compile time by default
for substantial performance gains in CPU usage and improved compile times. If
you need to access debug/trace log levels, you will need to build without the
release_max_log_level feature or use our provided static debug binaries.
Changing log level dynamically
conduwuit supports changing the tracing log environment filter on-the-fly using
the admin command !admin debug change-log-level <log env filter>. This accepts
a string without quotes the same format as the log config option.
Example: !admin debug change-log-level debug
This can also accept complex filters such as:
!admin debug change-log-level info,conduit_service[{dest="example.com"}]=trace,ruma_state_res=trace
!admin debug change-log-level info,conduit_service[{dest="example.com"}]=trace,conduit_service[send{dest="example.org"}]=trace
And to reset the log level to the one that was set at startup / last config
load, simply pass the --reset flag.
!admin debug change-log-level --reset
Pinging servers
conduwuit can ping other servers using !admin debug ping <server>. This takes
a server name and goes through the server discovery process and queries
/_matrix/federation/v1/version. Errors are outputted.
While it does measure the latency of the request, it is not indicative of server performance on either side as that endpoint is completely unauthenticated and simply fetches a string on a static JSON endpoint. It is very low cost both bandwidth and computationally.
Allocator memory stats
When using jemalloc with jemallocator's stats feature (--enable-stats), you
can see conduwuit's high-level allocator stats by using
!admin server memory-usage at the bottom.
If you are a developer, you can also view the raw jemalloc statistics with
!admin debug memory-stats. Please note that this output is extremely large
which may only be visible in the conduwuit console CLI due to PDU size limits,
and is not easy for non-developers to understand.
Development
Information about developing the project. If you are only interested in using it, you can safely ignore this page. If you plan on contributing, see the contributor's guide.
conduwuit project layout
conduwuit uses a collection of sub-crates, packages, or workspace members
that indicate what each general area of code is for. All of the workspace
members are under src/. The workspace definition is at the top level / root
Cargo.toml.
The crate names are generally self-explanatory:
adminis the admin roomapiis the HTTP API, Matrix C-S and S-S endpoints, etccoreis core conduwuit functionality like config loading, error definitions, global utilities, logging infrastructure, etcdatabaseis RocksDB methods, helpers, RocksDB config, and general database definitions, utilities, or functionsmacrosare conduwuit Rust macros like general helper macros, logging and error handling macros, and syn and procedural macros used for admin room commands and othersmainis the "primary" sub-crate. This is where themain()function lives, tokio worker and async initialisation, Sentry initialisation, clap init, and signal handling. If you are adding new Rust features, they must go here.routeris the webserver and request handling bits, using axum, tower, tower-http, hyper, etc, and the global server state to accessservices.serviceis the high-level database definitions and functions for data, outbound/sending code, and other business logic such as media fetching.
It is highly unlikely you will ever need to add a new workspace member, but if you truly find yourself needing to, we recommend reaching out to us in the Matrix room for discussions about it beforehand.
The primary inspiration for this design was apart of hot reloadable development,
to support "conduwuit as a library" where specific parts can simply be swapped out.
There is evidence Conduit wanted to go this route too as axum is technically an
optional feature in Conduit, and can be compiled without the binary or axum library
for handling inbound web requests; but it was never completed or worked.
See the Rust documentation on Workspaces for general questions and information on Cargo workspaces.
Adding compile-time features
If you'd like to add a compile-time feature, you must first define it in
the main workspace crate located in src/main/Cargo.toml. The feature must
enable a feature in the other workspace crate(s) you intend to use it in. Then
the said workspace crate(s) must define the feature there in its Cargo.toml.
So, if this is adding a feature to the API such as woof, you define the feature
in the api crate's Cargo.toml as woof = []. The feature definition in main's
Cargo.toml will be woof = ["conduwuit-api/woof"].
The rationale for this is due to Rust / Cargo not supporting "workspace level features", we must make a choice of; either scattering features all over the workspace crates, making it difficult for anyone to add or remove default features; or define all the features in one central workspace crate that propagate down/up to the other workspace crates. It is a Cargo pitfall, and we'd like to see better developer UX in Rust's Workspaces.
Additionally, the definition of one single place makes "feature collection" in our
Nix flake a million times easier instead of collecting and deduping them all from
searching in all the workspace crates' Cargo.tomls. Though we wouldn't need to
do this if Rust supported workspace-level features to begin with.
List of forked dependencies
During conduwuit development, we have had to fork some dependencies to support our use-cases in some areas. This ranges from things said upstream project won't accept for any reason, faster-paced development (unresponsive or slow upstream), conduwuit-specific usecases, or lack of time to upstream some things.
- ruma/ruma: https://github.com/girlbossceo/ruwuma - various performance improvements, more features, faster-paced development, better client/server interop hacks upstream won't accept, etc
- facebook/rocksdb: https://github.com/girlbossceo/rocksdb - liburing build fixes and GCC debug build fix
- tikv/jemallocator: https://github.com/girlbossceo/jemallocator - musl builds seem to be broken on upstream, fixes some broken/suspicious code in places, additional safety measures, and support redzones for Valgrind
- zyansheep/rustyline-async:
https://github.com/girlbossceo/rustyline-async - tab completion callback and
CTRL+\signal quit event for conduwuit console CLI - rust-rocksdb/rust-rocksdb:
https://github.com/girlbossceo/rust-rocksdb-zaidoon1 -
@zaidoon1's fork has quicker updates, more up to date dependencies, etc. Our fork fixes musl build issues, removes unnecessarygtestinclude, and uses our RocksDB and jemallocator forks. - tokio-rs/tracing: https://github.com/girlbossceo/tracing - Implements
CloneforEnvFilterto support dynamically changing tracing envfilter's alongside other logging/metrics things
Debugging with tokio-console
tokio-console can be a useful tool for debugging and profiling. To make a
tokio-console-enabled build of conduwuit, enable the tokio_console feature,
disable the default release_max_log_level feature, and set the --cfg tokio_unstable flag to enable experimental tokio APIs. A build might look like
this:
RUSTFLAGS="--cfg tokio_unstable" cargo +nightly build \
--release \
--no-default-features \
--features=systemd,element_hacks,gzip_compression,brotli_compression,zstd_compression,tokio_console
You will also need to enable the tokio_console config option in conduwuit when
starting it. This was due to tokio-console causing gradual memory leak/usage
if left enabled.
Contributing guide
This page is for about contributing to conduwuit. The development page may be of interest for you as well.
If you would like to work on an issue that is not assigned, preferably ask in the Matrix room first at #conduwuit:puppygock.gay, and comment on it.
Linting and Formatting
It is mandatory all your changes satisfy the lints (clippy, rustc, rustdoc, etc)
and your code is formatted via the nightly cargo fmt. A lot of the
rustfmt.toml features depend on nightly toolchain. It would be ideal if they
weren't nightly-exclusive features, but they currently still are. CI's rustfmt
uses nightly.
If you need to allow a lint, please make sure it's either obvious as to why (e.g. clippy saying redundant clone but it's actually required) or it has a comment saying why. Do not write inefficient code for the sake of satisfying lints. If a lint is wrong and provides a more inefficient solution or suggestion, allow the lint and mention that in a comment.
Running CI tests locally
conduwuit's CI for tests, linting, formatting, audit, etc use
engage. engage can be installed from nixpkgs or cargo install engage. conduwuit's Nix flake devshell has the nixpkgs engage with direnv.
Use engage --help for more usage details.
To test, format, lint, etc that CI would do, install engage, allow the .envrc
file using direnv allow, and run engage.
All of the tasks are defined at the engage.toml file. You can
view all of them neatly by running engage list
If you would like to run only a specific engage task group, use just:
engage just <group>- Example:
engage just lints
If you would like to run a specific engage task in a specific group, use just <GROUP> [TASK]: engage just lints cargo-fmt
The following binaries are used in engage.toml:
engagenixdirenvrustccargocargo-fmtrustdoccargo-clippycargo-auditcargo-deblycheemarkdownlint-clidpkg
Matrix tests
CI runs Complement, but currently does not fail if results from the checked-in results differ with the new results. If your changes are done to fix Matrix tests, note that in your pull request. If more Complement tests start failing from your changes, please review the logs (they are uploaded as artifacts) and determine if they're intended or not.
If you'd like to run Complement locally using Nix, see the testing page.
Sytest support will come soon.
Writing documentation
conduwuit's website uses mdbook and deployed via CI using GitHub
Pages in the documentation.yml workflow file with Nix's
mdbook in the devshell. All documentation is in the docs/ directory at the top
level. The compiled mdbook website is also uploaded as an artifact.
To build the documentation using Nix, run: bin/nix-build-and-cache just .#book
The output of the mdbook generation is in result/. mdbooks can be opened in
your browser from the individual HTML files without any web server needed.
Inclusivity and Diversity
All MUST code and write with inclusivity and diversity in mind. See the following page by Google on writing inclusive code and documentation.
This EXPLICITLY forbids usage of terms like "blacklist"/"whitelist" and "master"/"slave", forbids gender-specific words and phrases, forbids ableist language like "sanity-check", "cripple", or "insane", and forbids culture-specific language (e.g. US-only holidays or cultures).
No exceptions are allowed. Dependencies that may use these terms are allowed but do not replicate the name in your functions or variables.
In addition to language, write and code with the user experience in mind. This is software that intends to be used by everyone, so make it easy and comfortable for everyone to use. 🏳️⚧️
Variable, comment, function, etc standards
Rust's default style and standards with regards to function names, variable names, comments, etc applies here.
Creating pull requests
Please try to keep contributions to the GitHub. While the mirrors of conduwuit allow for pull/merge requests, there is no guarantee I will see them in a timely manner. Additionally, please mark WIP or unfinished or incomplete PRs as drafts. This prevents me from having to ping once in a while to double check the status of it, especially when the CI completed successfully and everything so it looks done.
If you open a pull request on one of the mirrors, it is your responsibility to
inform me about its existence. In the future I may try to solve this with more
repo bots in the conduwuit Matrix room. There is no mailing list or email-patch
support on the sr.ht mirror, but if you'd like to email me a git patch you can
do so at strawberry@puppygock.gay.
Direct all PRs/MRs to the main branch.
By sending a pull request or patch, you are agreeing that your changes are allowed to be licenced under the Apache-2.0 licence and all of your conduct is in line with the Contributor's Covenant, and conduwuit's Code of Conduct.
Contribution by users who violate either of these code of conducts will not have their contributions accepted. This includes users who have been banned from conduwuit Matrix rooms for Code of Conduct violations.
Testing
Complement
Have a look at Complement's repository for an explanation of what it is.
To test against Complement, with Nix (or Lix and
direnv installed and set up (run direnv allow after setting up the hook), you can:
- Run
./bin/complement "$COMPLEMENT_SRC"to build a Complement image, run the tests, and output the logs and results to the specified paths. This will also output the OCI image atresult - Run
nix build .#complementfrom the root of the repository to just build a Complement OCI image outputted toresult(it's a.tar.gzfile) - Or download the latest Complement OCI image from the CI workflow artifacts output from the commit/revision you want to test (e.g. from main) here
If you want to use your own prebuilt OCI image (such as from our CI) without needing
Nix installed, put the image at complement_oci_image.tar.gz in the root of the repo
and run the script.
If you're on macOS and need to build an image, run nix build .#linux-complement.
We have a Complement fork as some tests have needed to be fixed. This can be found at: https://github.com/girlbossceo/complement
Hot Reloading ("Live" Development)
Note that hot reloading has not been refactored in quite a while and is not guaranteed to work at this time.
Summary
When developing in debug-builds with the nightly toolchain, conduwuit is modular
using dynamic libraries and various parts of the application are hot-reloadable
while the server is running: http api handlers, admin commands, services,
database, etc. These are all split up into individual workspace crates as seen
in the src/ directory. Changes to sourcecode in a crate rebuild that crate and
subsequent crates depending on it. Reloading then occurs for the changed crates.
Release builds still produce static binaries which are unaffected. Rust's soundness guarantees are in full force. Thus you cannot hot-reload release binaries.
Requirements
Currently, this development setup only works on x86_64 and aarch64 Linux glibc.
musl explicitly does not support hot reloadable libraries, and does not
implement dlclose. macOS does not fully support our usage of RTLD_GLOBAL
possibly due to some thread-local issues. This Rust issue may be of
relevance, specifically this comment. It may be possible to get it working
on only very modern macOS versions such as at least Sonoma, as currently loading
dylibs is supported, but not unloading them in our setup, and the cited comment
mentions an Apple WWDC confirming there have been TLS changes to somewhat make
this possible.
As mentioned above this requires the nightly toolchain. This is due to reliance
on various Cargo.toml features that are only available on nightly, most
specifically RUSTFLAGS in Cargo.toml. Some of the implementation could also be
simpler based on other various nightly features. We hope lots of nightly
features start making it out of nightly sooner as there have been dozens of very
helpful features that have been stuck in nightly ("unstable") for at least 5+
years that would make this simpler. We encourage greater community consensus to
move these features into stability.
This currently only works on x86_64/aarch64 Linux with a glibc C library. musl C
library, macOS, and likely other host architectures are not supported (if other
architectures work, feel free to let us know and/or make a PR updating this).
This should work on GNU ld and lld (rust-lld) and gcc/clang, however if you
happen to have linker issues it's recommended to try using mold or gold
linkers, and please let us know in the conduwuit Matrix room the linker
error and what linker solved this issue so we can figure out a solution. Ideally
there should be minimal friction to using this, and in the future a build script
(build.rs) may be suitable to making this easier to use if the capabilities
allow us.
Usage
As of 19 May 2024, the instructions for using this are:
-
Have patience. Don't hesitate to join the conduwuit Matrix room to receive help using this. As indicated by the various rustflags used and some of the interesting issues linked at the bottom, this is definitely not something the Rust ecosystem or toolchain is used to doing.
-
Install the nightly toolchain using rustup. You may need to use
rustup override set nightlyin your local conduwuit directory, or usecargo +nightlyfor all actions. -
Uncomment
cargo-featuresat the top level / root Cargo.toml -
Scroll down to the
# Developer profilesection and uncomment ALL the rustflags for each dev profile and their respective packages. -
In each workspace crate's Cargo.toml (everything under
src/*ANDdeps/rust-rocksdb/Cargo.toml), uncomment thedylibcrate type under[lib]. -
Due to this rpath issue, you must export the
LD_LIBRARY_PATHenvironment variable to your nightly Rust toolchain library directory. If using rustup (hopefully), use this:export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:$HOME/.rustup/toolchains/nightly-x86_64-unknown-linux-gnu/lib/ -
Start the server. You can use
cargo +nightly runfor this along with the standard. -
Make some changes where you need to.
-
In a separate terminal window in the same directory (or using a terminal multiplexer like tmux), run the build Cargo command
cargo +nightly build. Cargo should only rebuild what was changed / what's necessary, so it should not be rebuilding all the crates. -
In your conduwuit server terminal, hit/send
CTRL+Csignal. This will tell conduwuit to find which libraries need to be reloaded, and reloads them as necessary. -
If there were no errors, it will tell you it successfully reloaded
#modules, and your changes should now be visible. Repeat 7 - 9 as needed.
To shutdown conduwuit in this setup, hit/send CTRL+\. Normal builds still
shutdown with CTRL+C as usual.
Steps 1 - 5 are the initial first-time steps for using this. To remove the hot reload setup, revert/comment all the Cargo.toml changes.
As mentioned in the requirements section, if you happen to have some linker
issues, try using the -fuse-ld= rustflag and specify mold or gold in all the
rustflags definitions in the top level Cargo.toml, and please let us know in
the conduwuit Matrix room the problem. mold can be installed typically
through your distro, and gold is provided by the binutils package.
It's possible a helper script can be made to do all of this, or most preferably
a specially made build script (build.rs). cargo watch support will be
implemented soon which will eliminate the need to manually run cargo build all
together.
Addendum
Conduit was inherited as a single crate without modularity or reloading in its design. Reasonable partitioning and abstraction allowed a split into several crates, though many circular dependencies had to be corrected. The resulting crates now form a directed graph as depicted in figures below. The interfacing between these crates is still extremely broad which is not mitigable.
Initially hot_lib_reload was investigated but found appropriate for a
project designed with modularity through limited interfaces, not a large and
complex existing codebase. Instead a bespoke solution built directly on
libloading satisfied our constraints. This required relatively minimal
modifications and zero maintenance burden compared to what would be required
otherwise. The technical difference lies with relocation processing: we leverage
global bindings (RTLD_GLOBAL) in a very intentional way. Most libraries and
off-the-shelf module systems (such as hot_lib_reload) restrict themselves
to local bindings (RTLD_LOCAL). This allows them to release software to
multiple platforms with much greater consistency, but at the cost of burdening
applications to explicitly manage these bindings. In our case with an optional
feature for developers, we shrug any such requirement to enjoy the cost/benefit
on platforms where global relocations are properly cooperative.
To make use of RTLD_GLOBAL the application has to be oriented as a directed
acyclic graph. The primary rule is simple and illustrated in the figure below:
no crate is allowed to call a function or use a variable from a crate below
it.
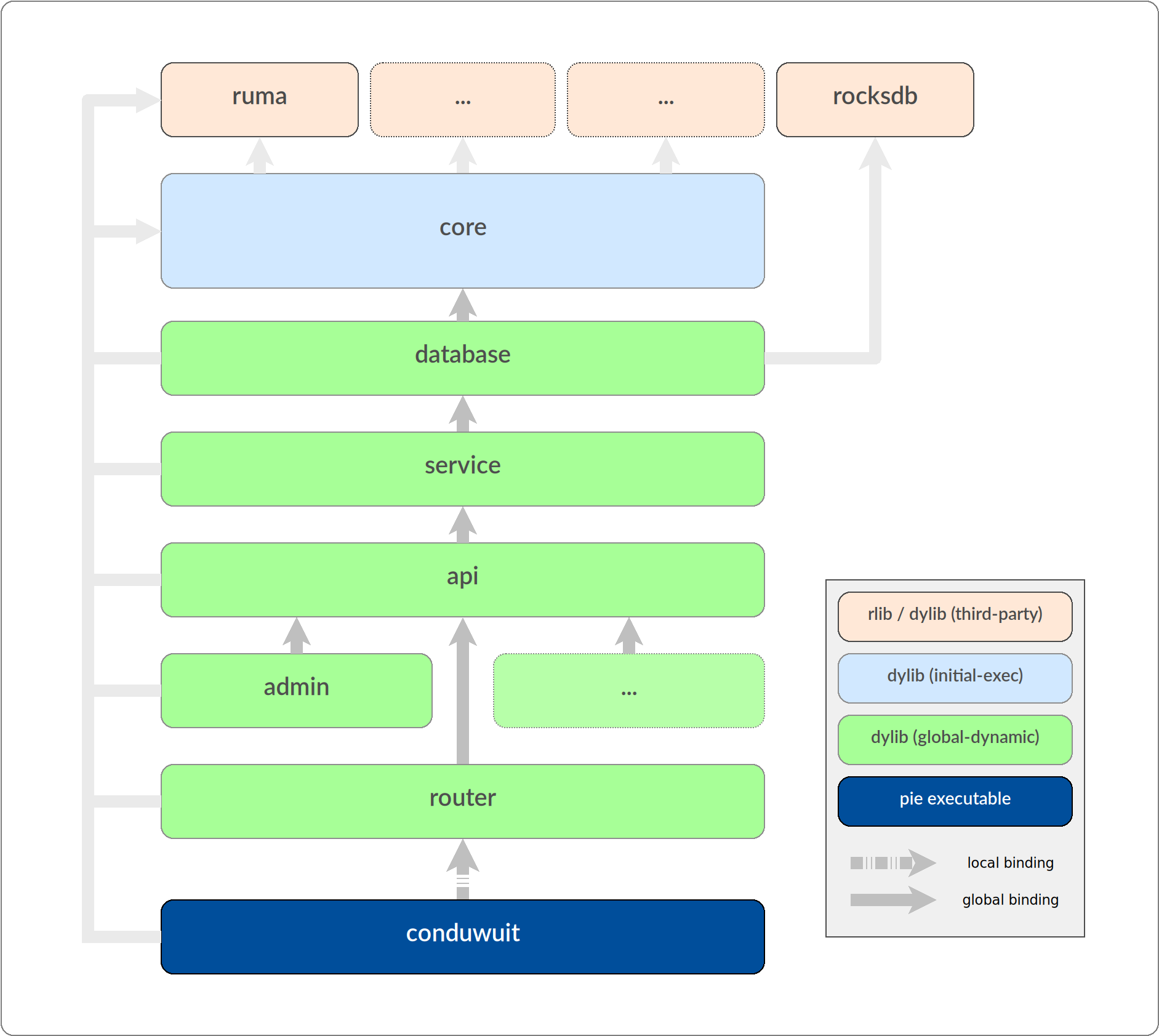
When a symbol is referenced between crates they become bound: crates cannot be
unloaded until their calling crates are first unloaded. Thus we start the
reloading process from the crate which has no callers. There is a small problem
though: the first crate is called by the base executable itself! This is solved
by using an RTLD_LOCAL binding for just one link between the main executable
and the first crate, freeing the executable from all modules as no global
binding ever occurs between them.
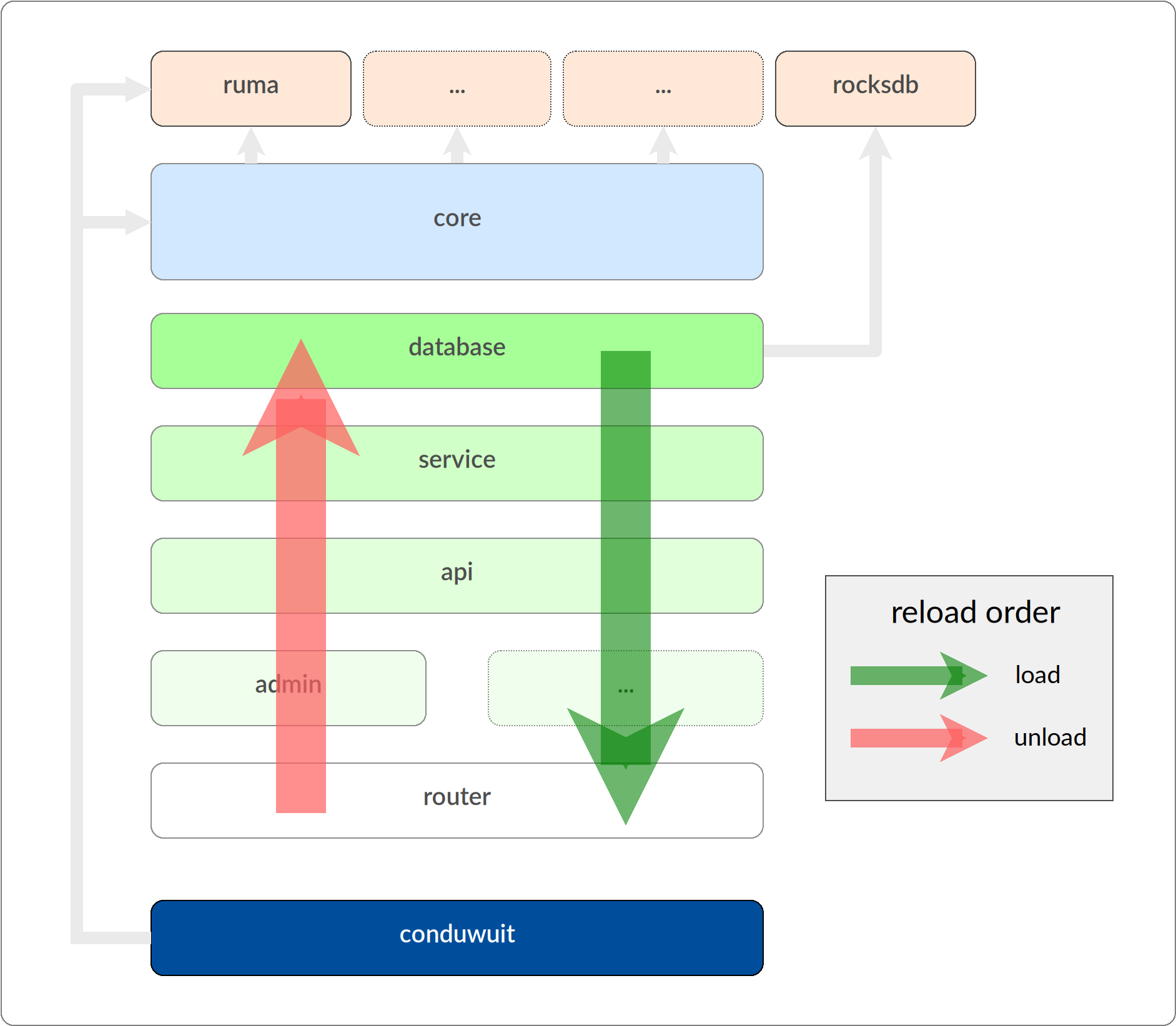
Proper resource management is essential for reliable reloading to occur. This is a very basic ask in RAII-idiomatic Rust and the exposure to reloading hazards is remarkably low, generally stemming from poor patterns and practices. Unfortunately static analysis doesn't enforce reload-safety programmatically (though it could one day), for now hazards can be avoided by knowing a few basic do's and dont's:
-
Understand that code is memory. Just like one is forbidden from referencing free'd memory, one must not transfer control to free'd code. Exposure to this is primarily from two things:
- Callbacks, which this project makes very little use of.
- Async tasks, which are addressed below.
-
Tie all resources to a scope or object lifetime with greatest possible symmetry (locality). For our purposes this applies to code resources, which means async blocks and tokio tasks.
- Never spawn a task without receiving and storing its JoinHandle.
- Always wait on join handles before leaving a scope or in another cleanup function called by an owning scope.
-
Know any minor specific quirks documented in code or here:
- Don't use
tokio::spawn, instead use ourHandleincore/server.rs, which is reachable in most of the codebase viaservices()or other state. This is due to some bugs or assumptions made in tokio, as it happens inunsafe {}blocks, which are mitigated by circumventing some thread-local variables. Using runtime handles is good practice in any case.
- Don't use
The initial implementation PR is available here.
Interesting related issues/bugs
- DT_RUNPATH produced in binary with rpath = true is wrong (cargo)
- Disabling MIR Optimization in Rust Compilation (cargo)
- Workspace-level metadata (cargo-deb)
conduwuit Community Code of Conduct
Welcome to the conduwuit community! We’re excited to have you here. conduwuit is a hard-fork of the Conduit homeserver, aimed at making Matrix more accessible and inclusive for everyone.
This space is dedicated to fostering a positive, supportive, and inclusive environment for everyone. This Code of Conduct applies to all conduwuit spaces, including any further community rooms that reference this CoC. Here are our guidelines to help maintain the welcoming atmosphere that sets conduwuit apart.
For the general foundational rules, please refer to the Contributor's Covenant. Below are additional guidelines specific to the conduwuit community.
Our Values and Guidelines
-
Respect and Inclusivity: We are committed to maintaining a community where everyone feels safe and respected. Discrimination, harassment, or hate speech of any kind will not be tolerated. Recognise that each community member experiences the world differently based on their past experiences, background, and identity. Share your own experiences and be open to learning about others' diverse perspectives.
-
Positivity and Constructiveness: Engage in constructive discussions and support each other. If you feel angry, negative, or aggressive, take a break until you can participate in a positive and constructive manner. Process intense feelings with a friend or in a private setting before engaging in community conversations to help maintain a supportive and focused environment.
-
Clarity and Understanding: Our community includes neurodivergent individuals and those who may not appreciate sarcasm or subtlety. Communicate clearly and kindly, avoiding sarcasm and ensuring your messages are easily understood by all. Additionally, avoid putting the burden of education on marginalized groups by doing your own research before asking for explanations.
-
Be Open to Inclusivity: Actively engage in conversations about making our community more inclusive. Report discriminatory behavior to the moderators and be open to constructive feedback that aims to improve our community. Understand that discussing discrimination and negative experiences can be emotionally taxing, so focus on the message rather than critiquing the tone used.
-
Commit to Inclusivity: Building an inclusive community requires time, energy, and resources. Recognise that addressing discrimination and bias is an ongoing process that necessitates commitment and action from all community members.
Matrix Community
This Code of Conduct applies to the entire conduwuit Matrix Space and its rooms, including:
#conduwuit:puppygock.gay
This room is for support and discussions about conduwuit. Ask questions, share insights, and help each other out.
#conduwuit-offtopic:girlboss.ceo
For off-topic community conversations about any subject. While this room allows for a wide range of topics, the same CoC applies. Keep discussions respectful and inclusive, and avoid divisive subjects like country/world politics. General topics, such as world events, are welcome as long as they follow the CoC.
#conduwuit-dev:puppygock.gay
This room is dedicated to discussing active development of conduwuit. Posting requires an elevated power level, which can be requested in one of the other rooms. Use this space to collaborate and innovate.
Enforcement
We have a zero-tolerance policy for violations of this Code of Conduct. If someone’s behavior makes you uncomfortable, please report it to the moderators. Actions we may take include:
- Warning: A warning given directly in the room or via a private message from the moderators, identifying the violation and requesting corrective action.
- Temporary Mute: Temporary restriction from participating in discussions for a specified period to allow for reflection and cooling off.
- Kick or Ban: Egregious behavior may result in an immediate kick or ban to protect other community members. Bans are considered permanent and will only be reversed in exceptional circumstances after proven good behavior.
Please highlight issues directly in rooms when possible, but if you don't feel comfortable doing that, then please send a DM to one of the moderators directly.
Together, let’s build a community where everyone feels valued and respected.
— The conduwuit Moderation Team